EC2 Instance Connect
Description
EC2 Instance Connect can be used to connect to instances using the Amazon EC2 console (browser-based client), the Amazon EC2 Instance Connect CLI, or the SSH client. Solution uses API to push a one-time-use SSH public key to the instance metadata where it remains for 60 seconds.
As for now (Q2 2021) Instance Connect supports following Linux distros:
- Amazon Linux 2 (any version)
- Ubuntu 16.04 or later
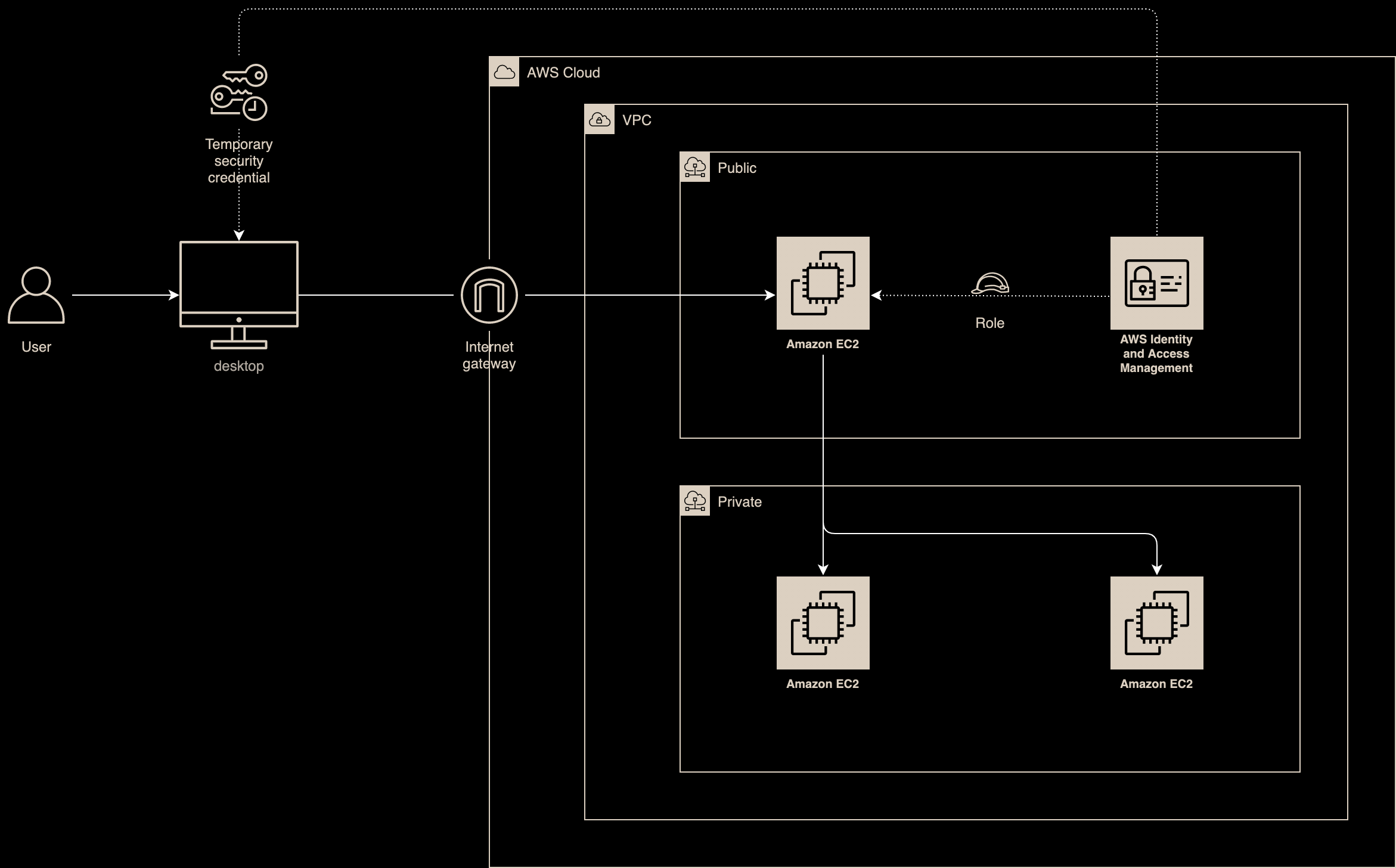
Lab Schema
Permissions
1a.Create Policy - RBAC scenario
Using any allowed method (CLI, AWS Console) create policy which will allow to establish connection using Instance Connect. Highlighted lines show how to allow access only to individual instances as well as allow login only using selected username.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2-instance-connect:SendSSHPublicKey",
"Resource": [
"arn:aws:ec2:region:account-id:instance/i-1234567890abcdef0",
"arn:aws:ec2:region:account-id:instance/i-0598c7d356eba48d7"
],
"Condition": {
"StringEquals": {
"ec2:osuser": "ami-username"
}
}
},
{
"Effect": "Allow",
"Action": "ec2:DescribeInstances",
"Resource": "*"
}
]
}
1b.Create Policy - ABAC scenario
Following example shows policy based on ABAC (Attribute-based access control). Access to instances is controlled by tags - only instances with proper key/value tag can be accessible via InstanceConnect.
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":"ec2-instance-connect:SendSSHPublicKey",
"Resource": "arn:aws:ec2:region:account-id:instance/*",
"Condition":{
"StringEquals":{
"aws:ResourceTag/tag-key":"tag-value"
}
}
},
{
"Effect": "Allow",
"Action": "ec2:DescribeInstances",
"Resource": "*"
}
]
}
2.Attach policy to IAM entity
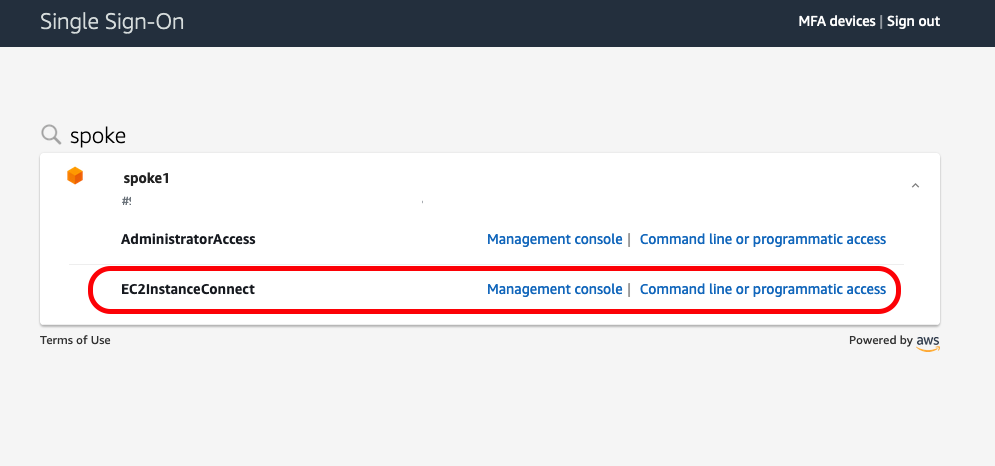
In our scenario, previously created policy will be attached to role which can be assumed by authenticated user via AWS SSO. To configure AWS SSO, follow below link
Software installation
Following step needs to be configured only if you are using image older than 2.0.20190618 (Amazon Linux 2) or 20.04 for (Ubuntu)
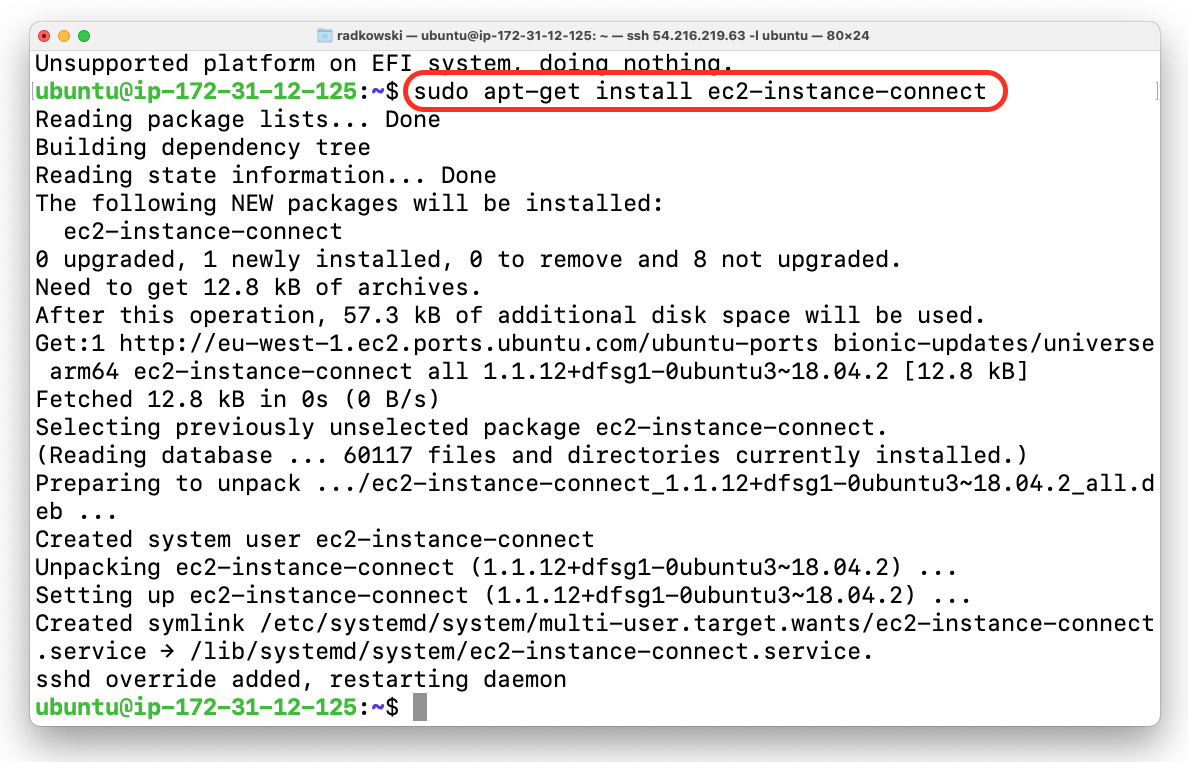
3.Install InstanceConnect
Log into target EC2 instance(s) and execute following command:
Amazon Linux 2:
[ec2-user ~]$ sudo yum -y update
[ec2-user ~]$ sudo yum install ec2-instance-connect
Ubuntu:
ubuntu:~$sudo apt-get updateubuntu:~$sudo apt-get upgradeubuntu:~$sudo apt-get install ec2-instance-connect
Connection via Instance Connect CLI
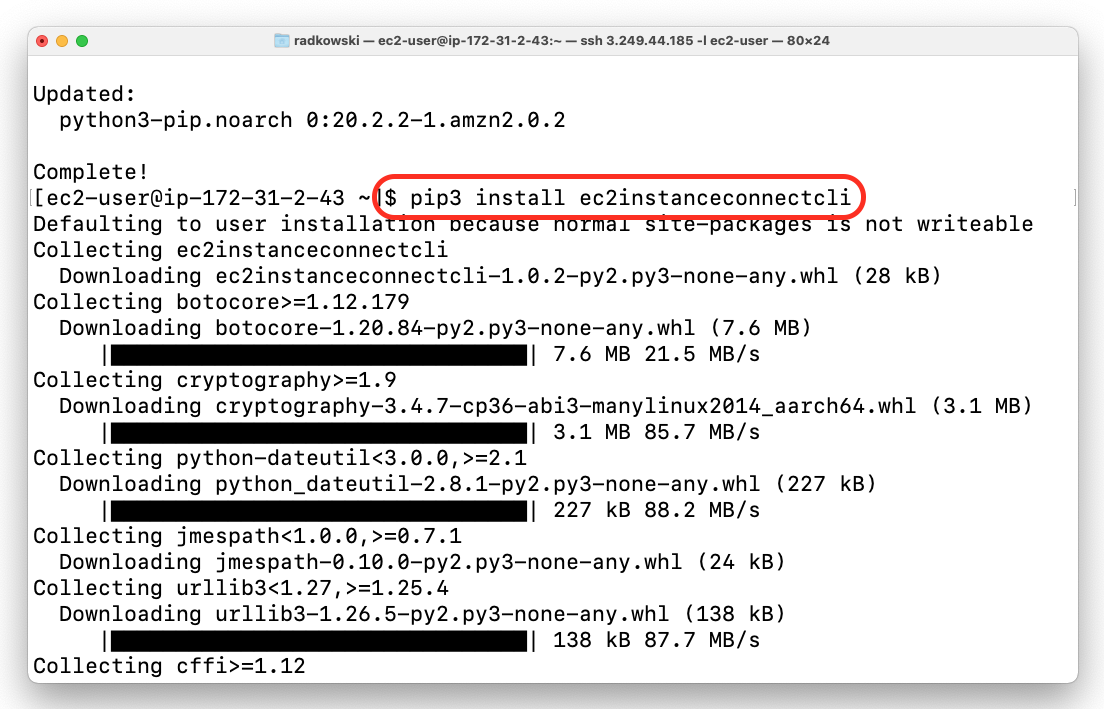
4a.EC2 Instance Connect CLI (#1)
To establish InstanceConnect session within AWS, attach to bastion host instance profile with policy defined in step #1. Next, log into instance and execute following commands (following example based on Amazon Linux):
$ sudo yum -y install python3-pip
$ pip3 install ec2instanceconnectcli4b.EC2 Instance Connect CLI (#2)
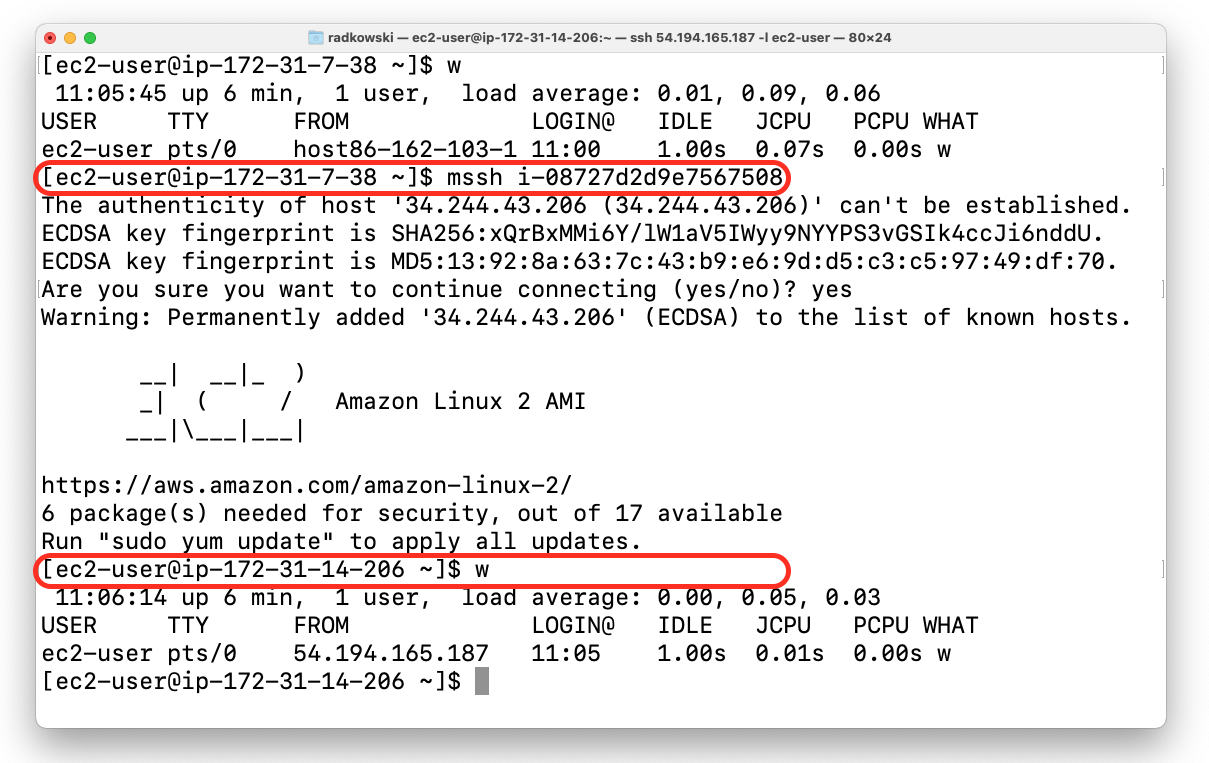
To establish connection you need to use mssh command and EC2 instance ID:
$ mssh i-1234567890abcdefConnection via SSH Client
5a.EC2 Instance Connect via SSH (#1)
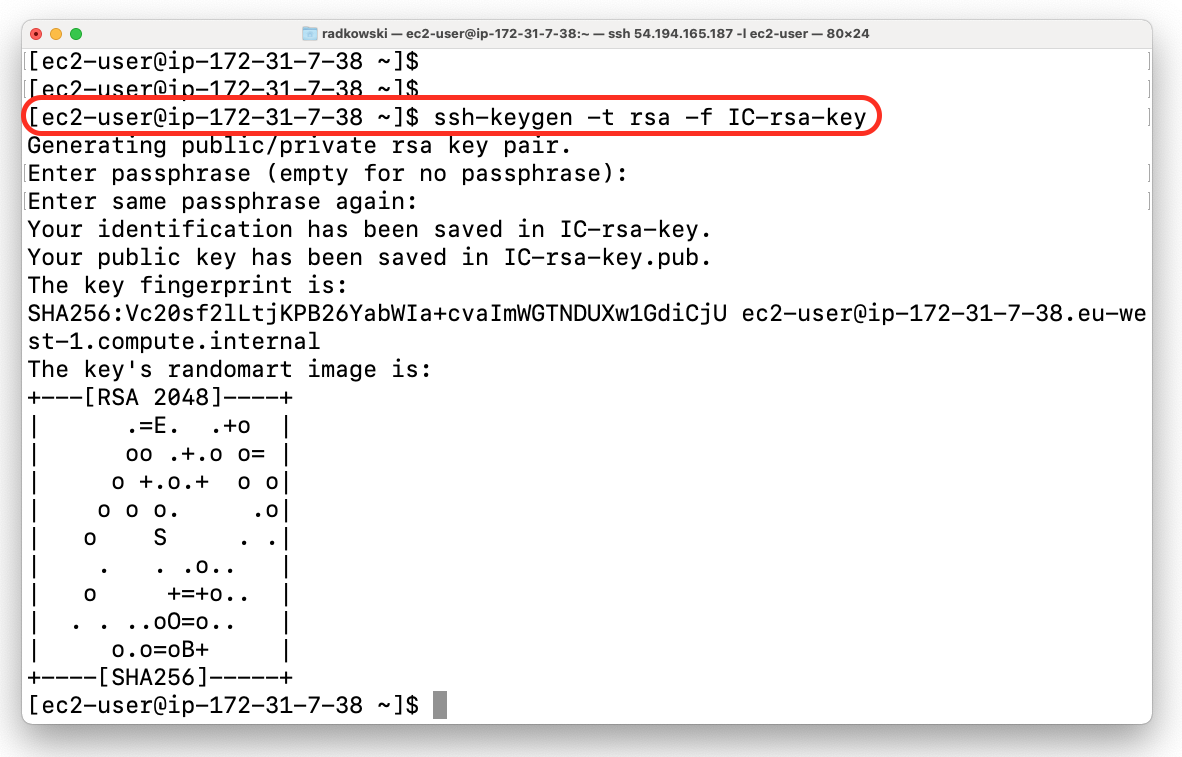
It's possible to use ssh client to connect via InstanceConnect, however couple of extra steps are required. Start with generating new key pair
$ ssh-keygen -t rsa -f IC-rsa-key5b.EC2 Instance Connect via SSH (#2)
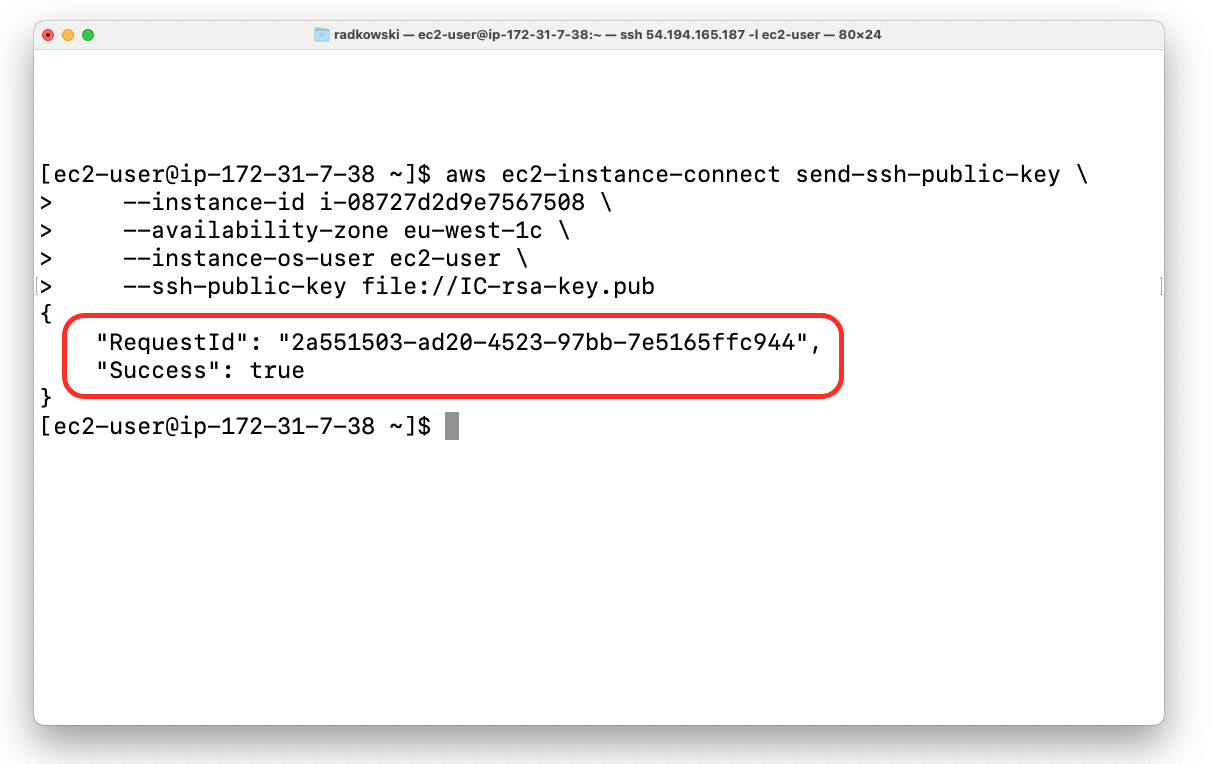
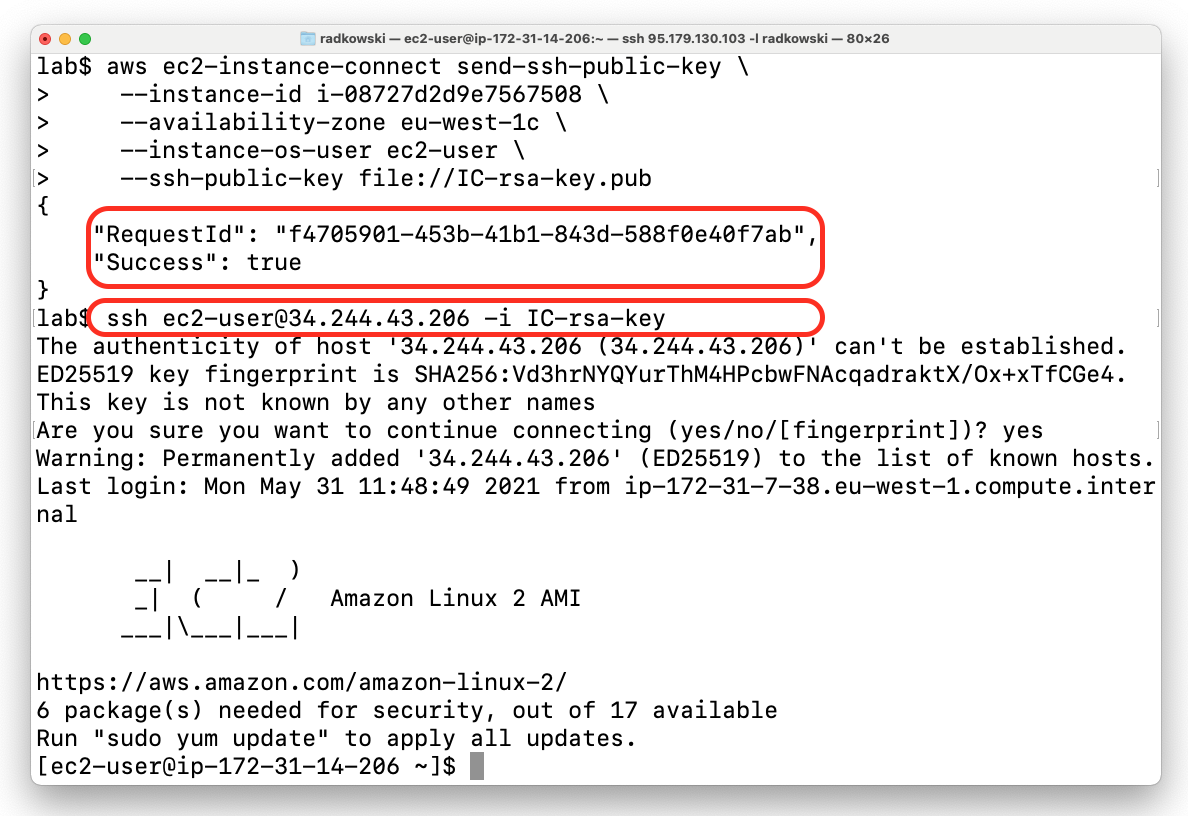
Next execute following command using awscli. You need to provide valid EC2 instance ID, AZ where EC2 is deployed and previously created public key:
aws ec2-instance-connect send-ssh-public-key \
--instance-id i-08727d2d9e7567508 \
--availability-zone eu-west-1c \
--instance-os-user ec2-user \
--ssh-public-key file://IC-rsa-key.pub5c.EC2 Instance Connect via SSH (#3)
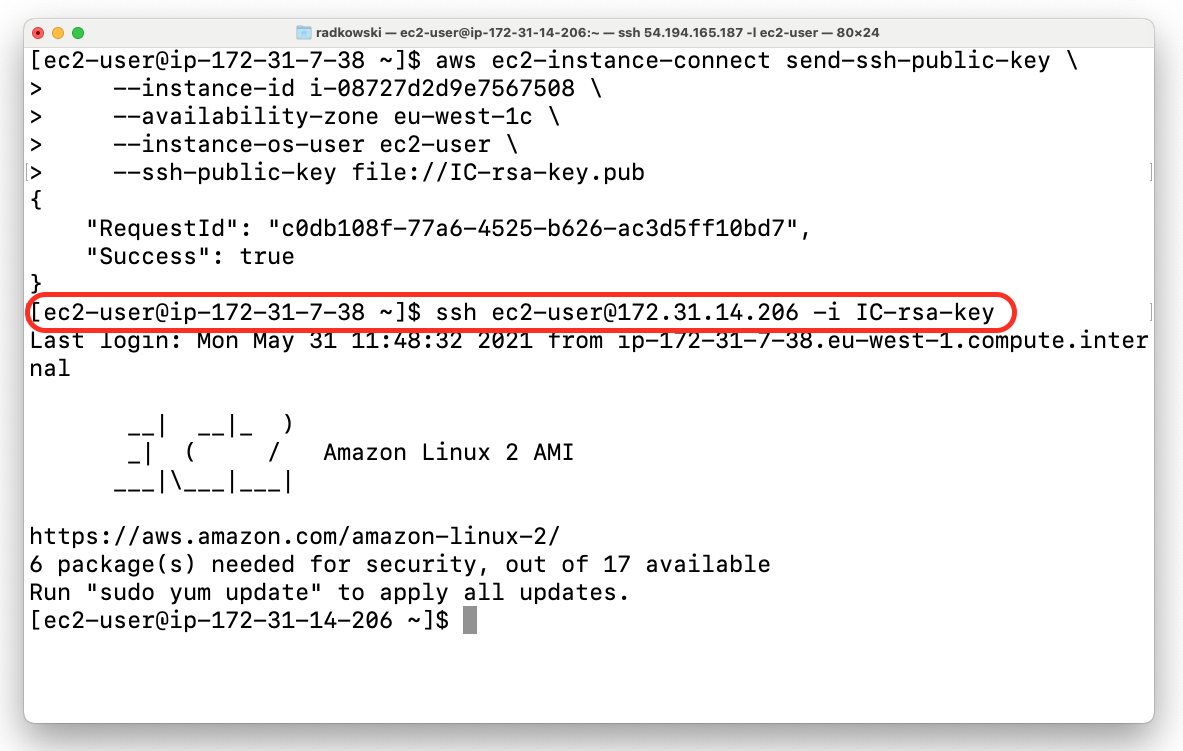
Now you can connect to Ec2 instance using private IP and key you have previously created. Bear in mind that key will be valid only 60 second !!!
ssh ec2-user@172.31.14.206 -i IC-rsa-keyConnection from the Internet via SSH Client
6.EC2 Instance Connect from outside AWS
Instance Connect works also if you are connecting AWS EC2 instance from the internet. Following example shows InstanceConnect session established from OpenBSD deployed outside AWS