DNS64 + NAT64 + v6only Subnet
Description
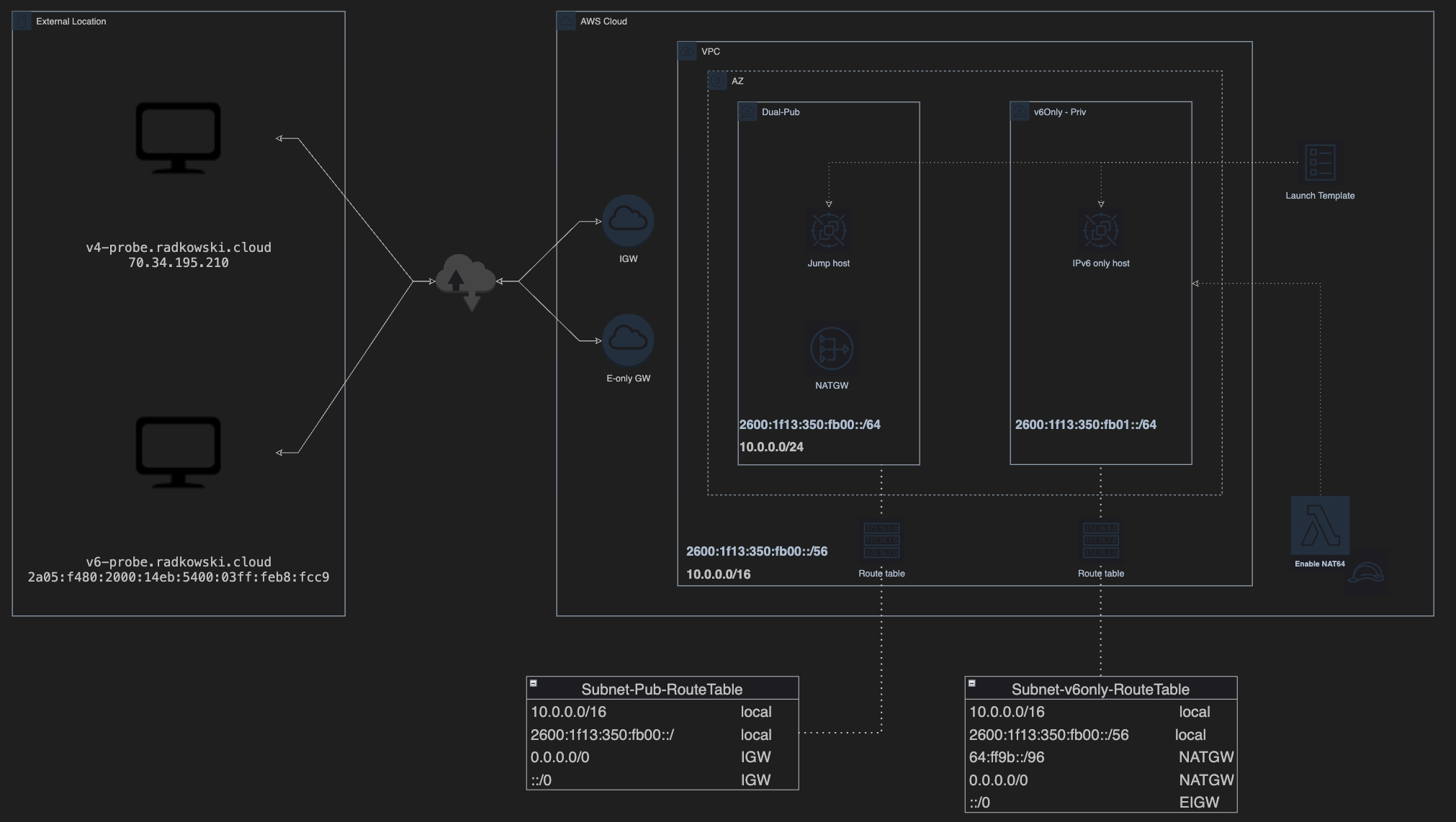
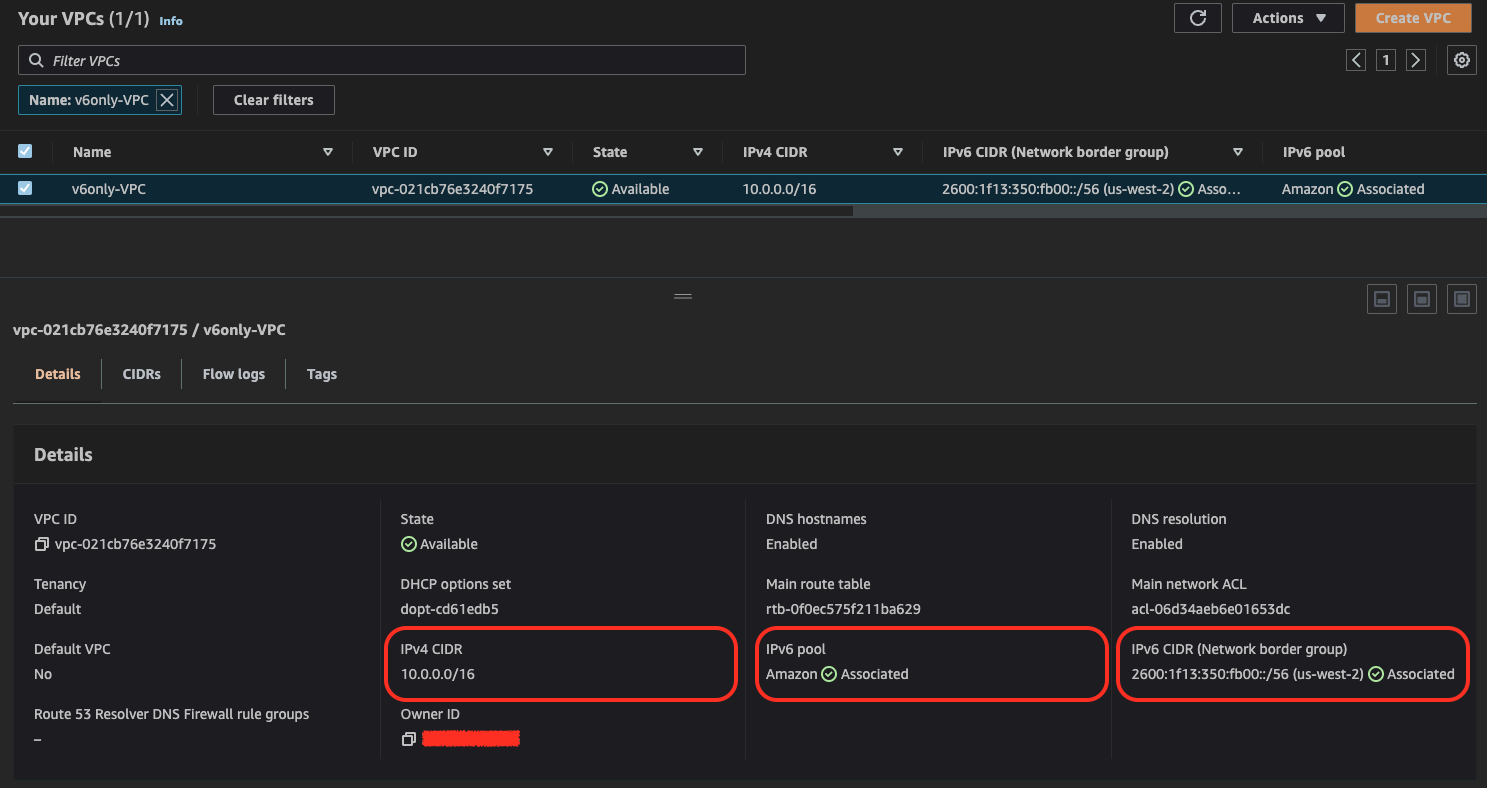
Since December 2021 AWS NAT Gateway supports network address translation from IPv6 to IPv4, popularly known as NAT64. NAT64 allows IPv6 AWS resources to communicate with IPv4 resources in the same VPC or a different VPC, in on-premises network, or over the internet. It can be used with DNS64 on Amazon Route 53 Resolver or self-managed DNS64 service. The above solutions can be used in conjunction with IPv6-only subnets in dual-stack VPCs released by AWS at the end of 2021.
IaC
Deployment scenarios
The following lab can be deployed manually using the Step-by-Step solution below or automatically using Terraform. If you choose the IaC way, clone code from the repo on the right, deploy using Terraform and jump directly to the "Test Area" section below.

Config
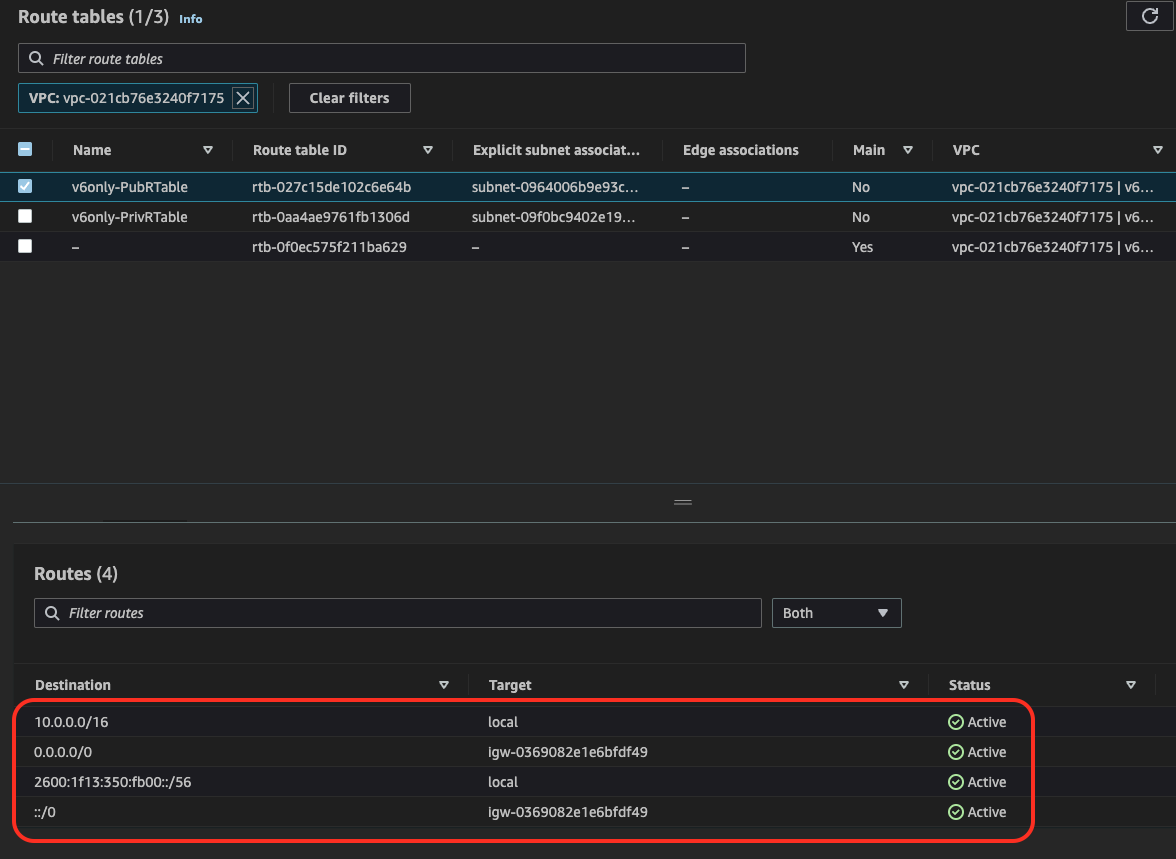
6. Create Public Route Table
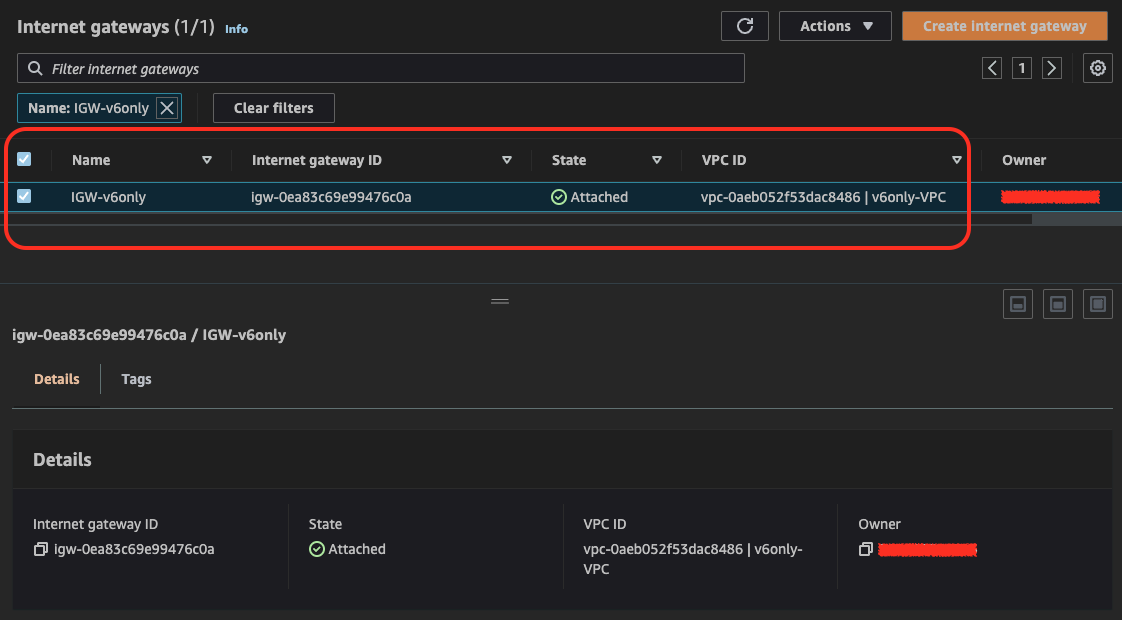
Create Public Route Table, associate Public Subnet and configure default route (both for IPv4 and IPv6) using Internet Gateway
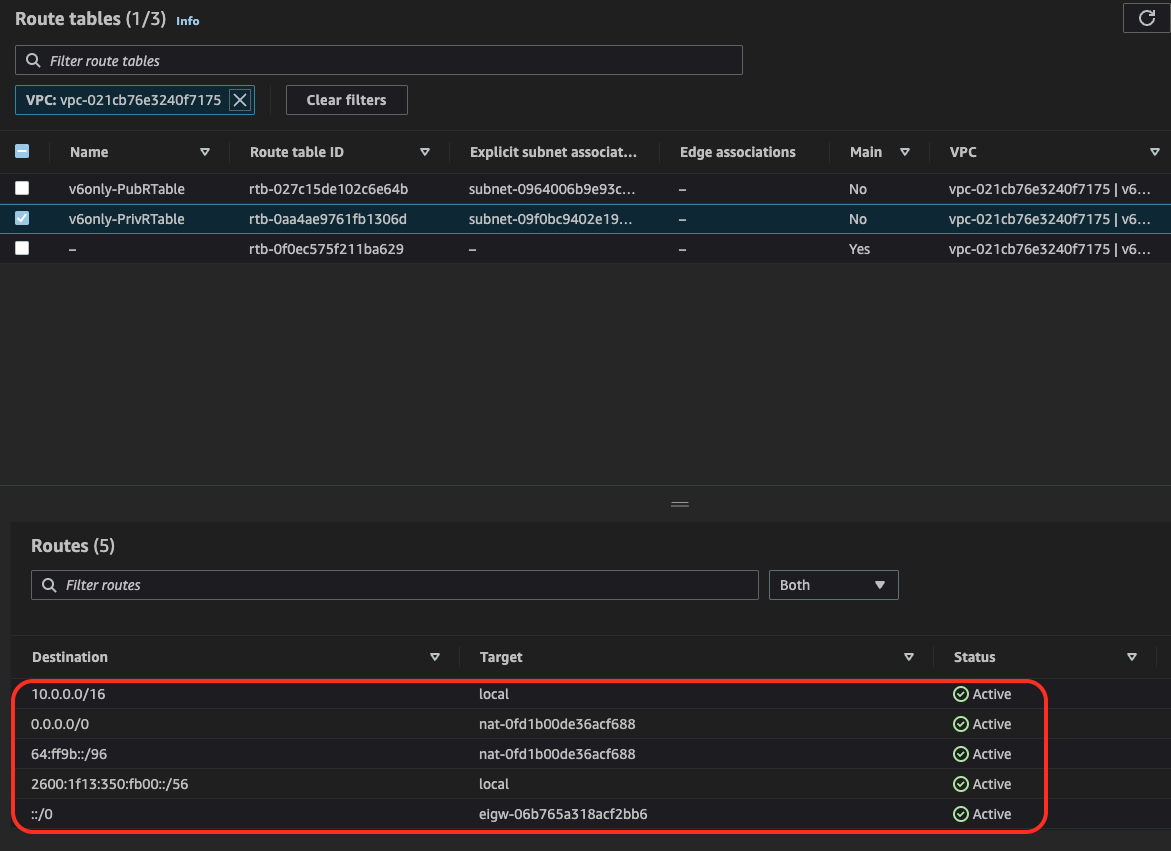
7. Create Private Route Table
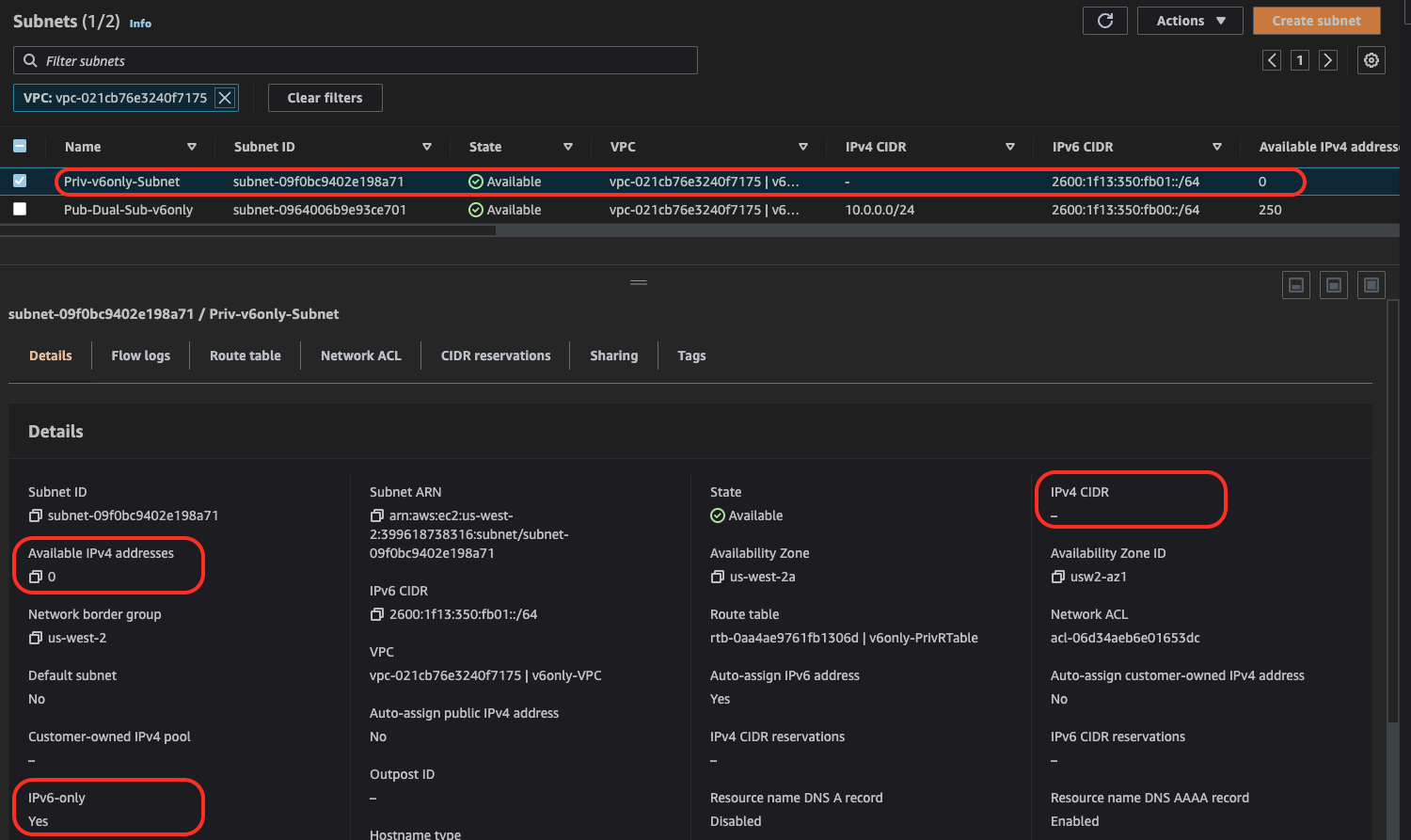
Create Private Route Table, associate Private Subnet and configure route based on following:
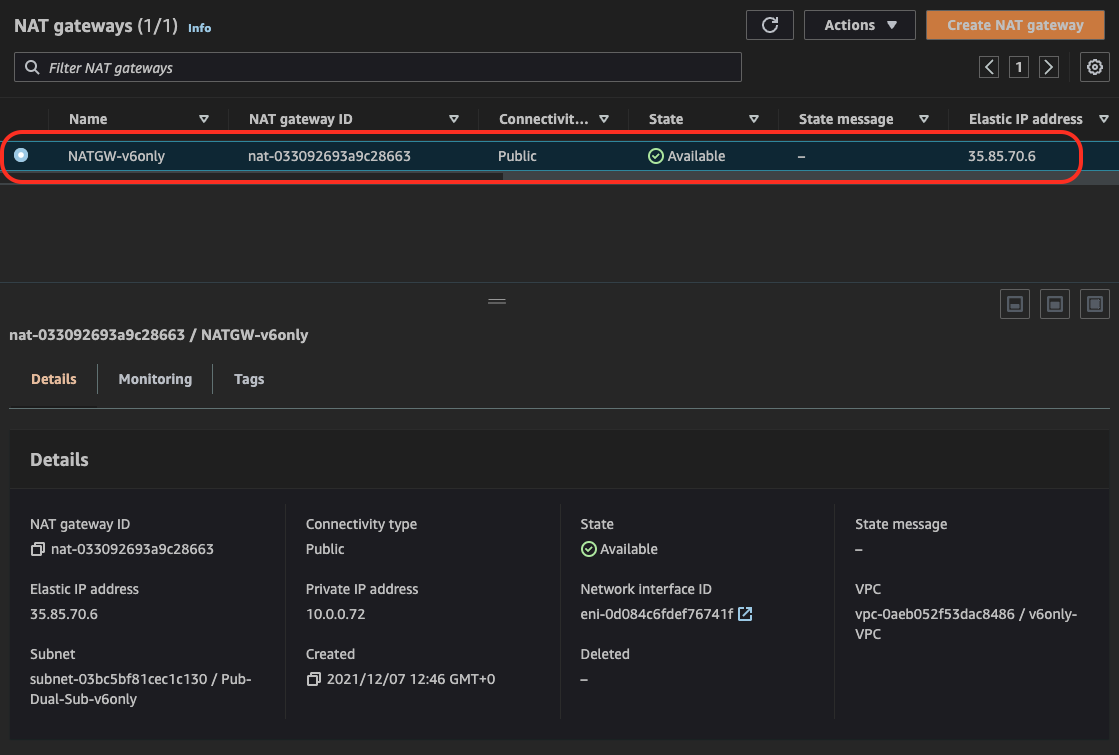
- 0.0.0.0/0 via NAT-Gateway
- 64:ff96::/96 via NAT Gateway
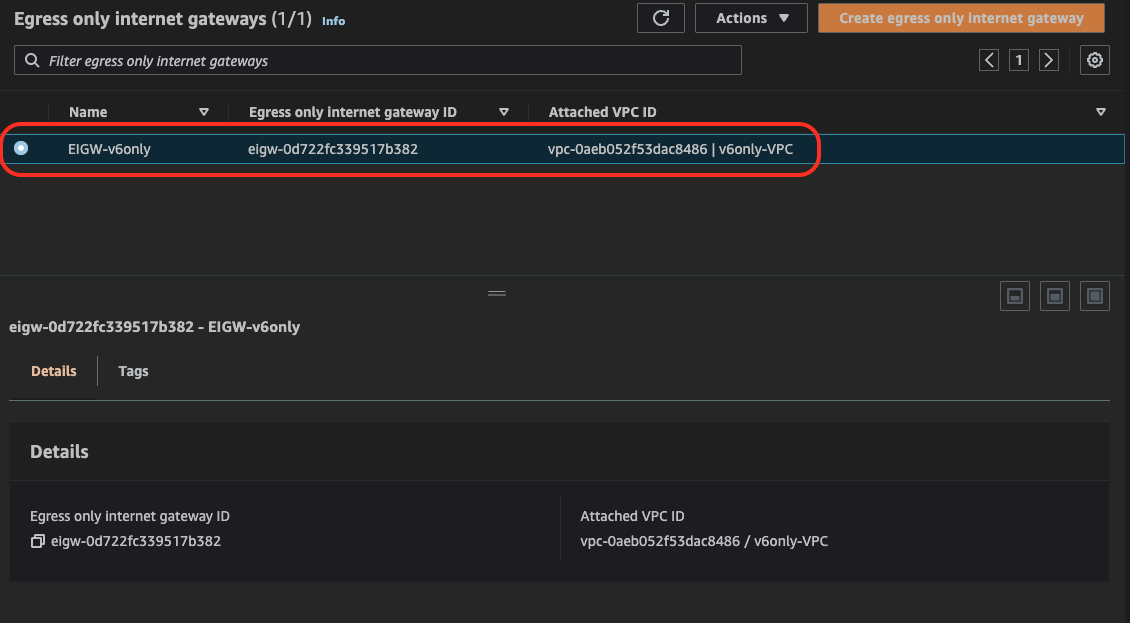
- ::/0 via Egress Only Gateway
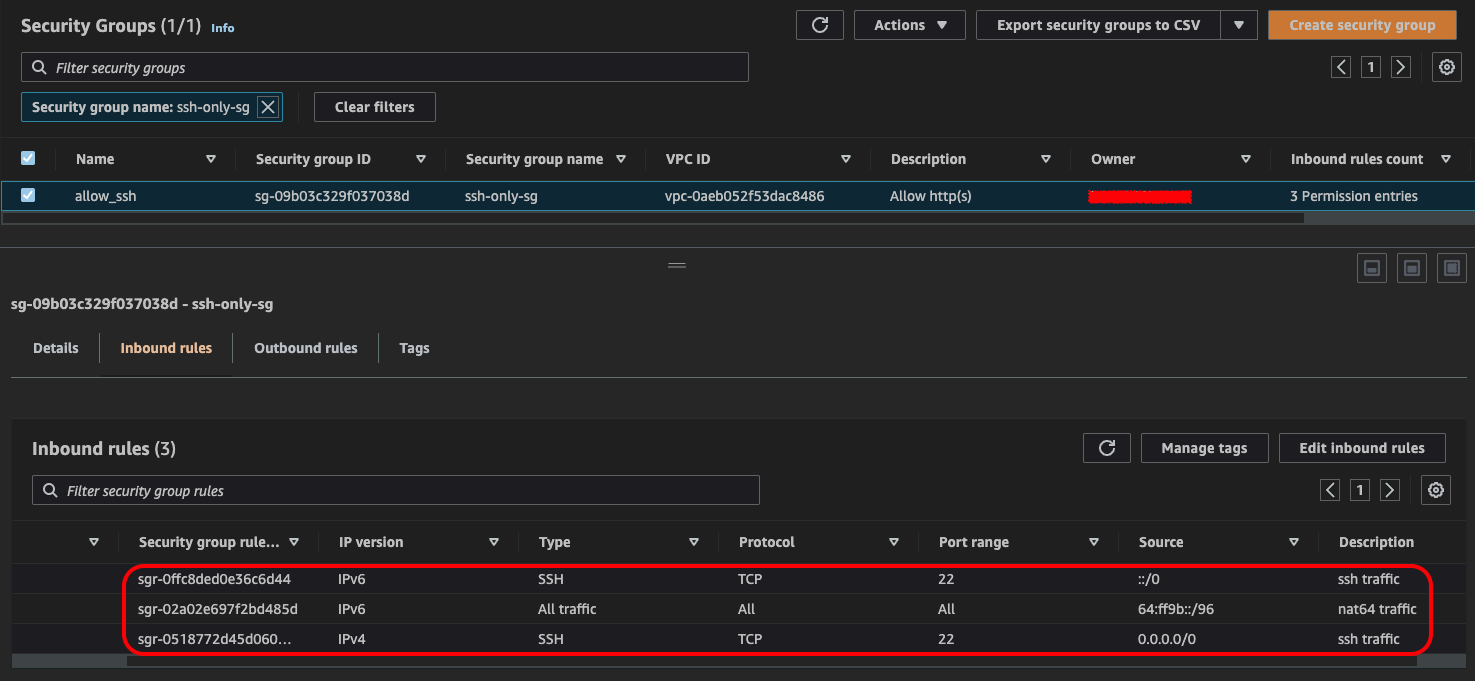
8. Create Security Groups
Configure security groups to allow traffic to test host including traffic from 64:ff9b::/96 subnet
Test Area
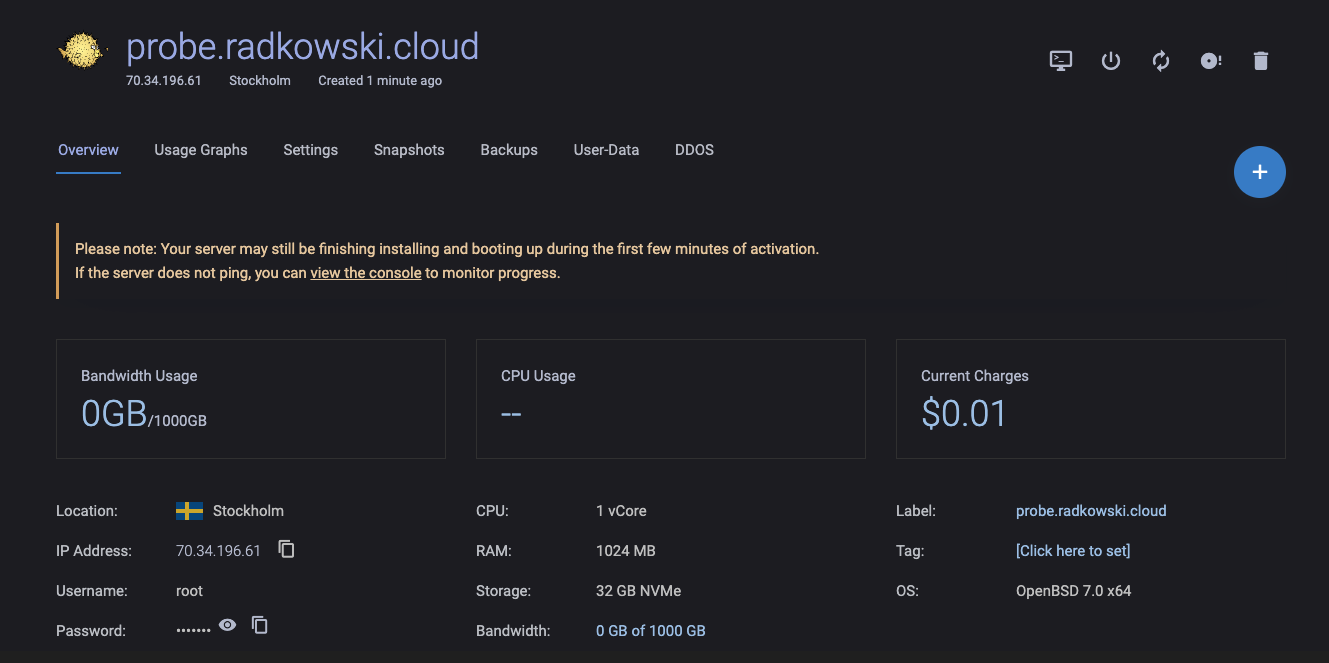
9. Create test server outside AWS
Create a host outside AWS that will be used as a probe. Assign both IPv4 and IPv6 addresses to it and configure DNS.
In lab scenario, following has been used:
- v4-probe.radkowski.cloud (A record)
- v6-probe.radkowski.cloud (AAAA record)
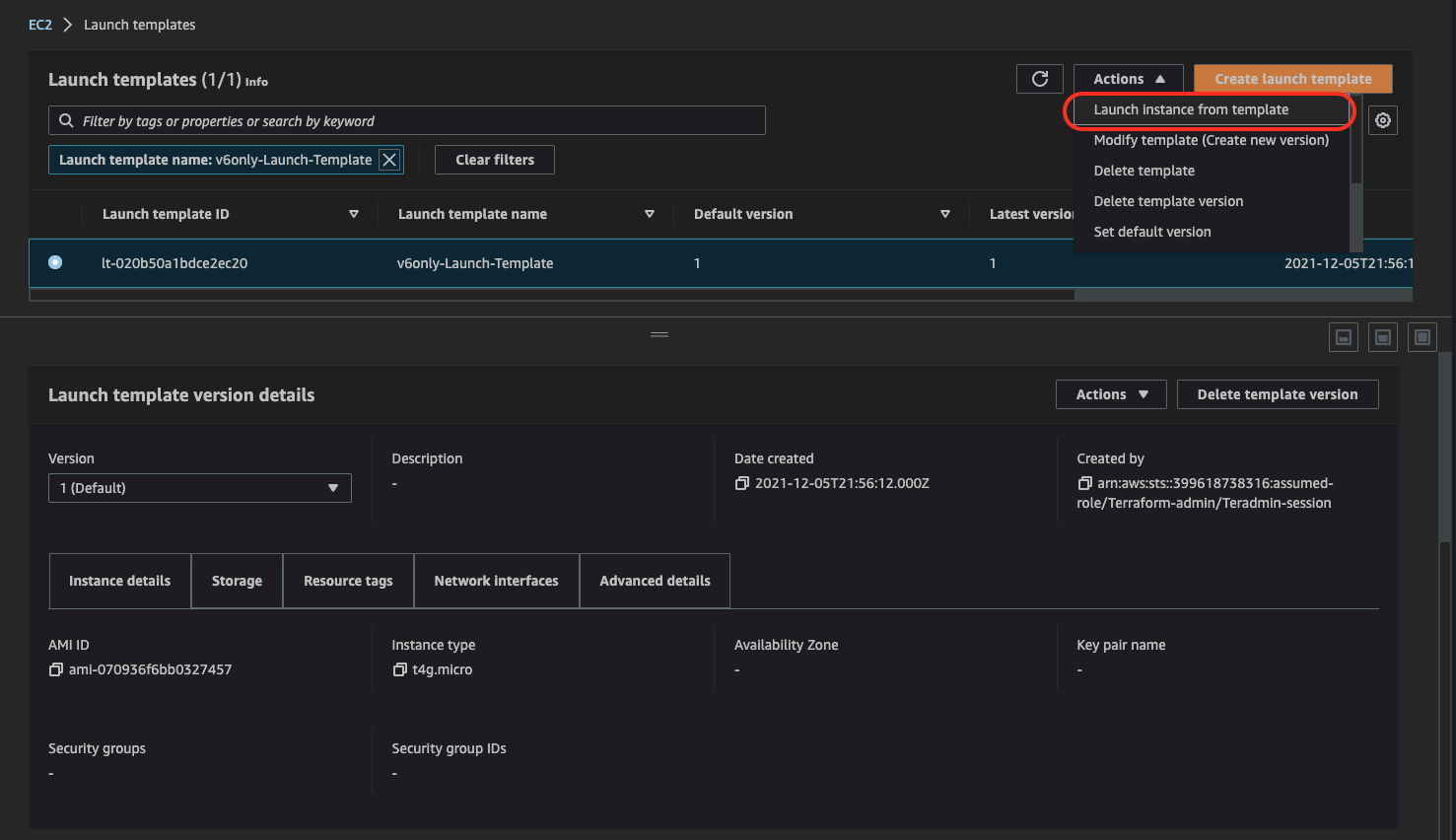
10. Launch v6-only EC2 Spot instance and jump host
If the solution has been deployed via TF (IaC section) you can use Launch Template to deploy two Spot instances:
- v6only-EC2 instance inside Private Subnet
- Jump host instance inside Public Subnet
For both instances use the security group selected in step #8
If the solution has not been deployed using IaC, deploy both instances manually
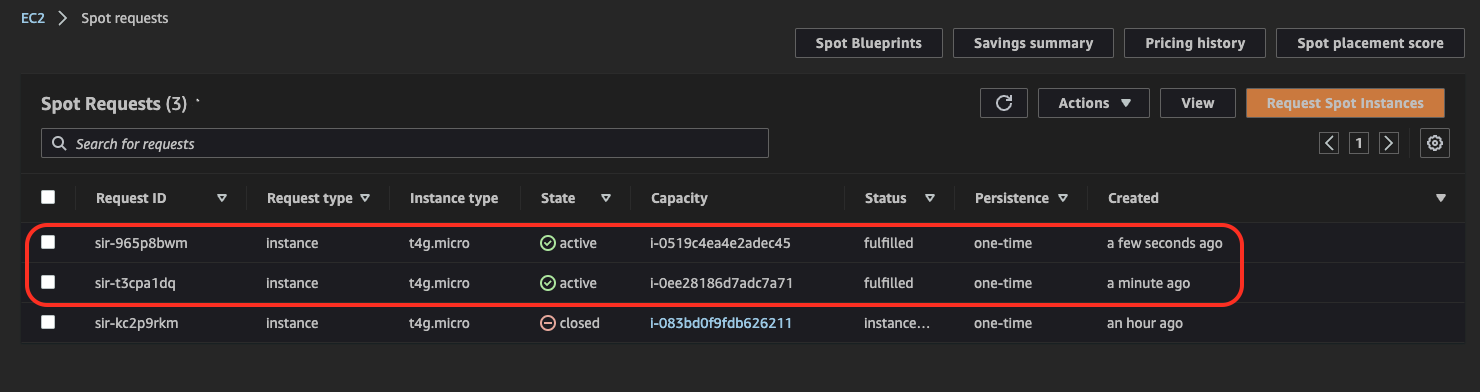
11. Confirm Spot Instances have been launched
For EC2 instances created by Launch Template, you should see two related Spot Requests
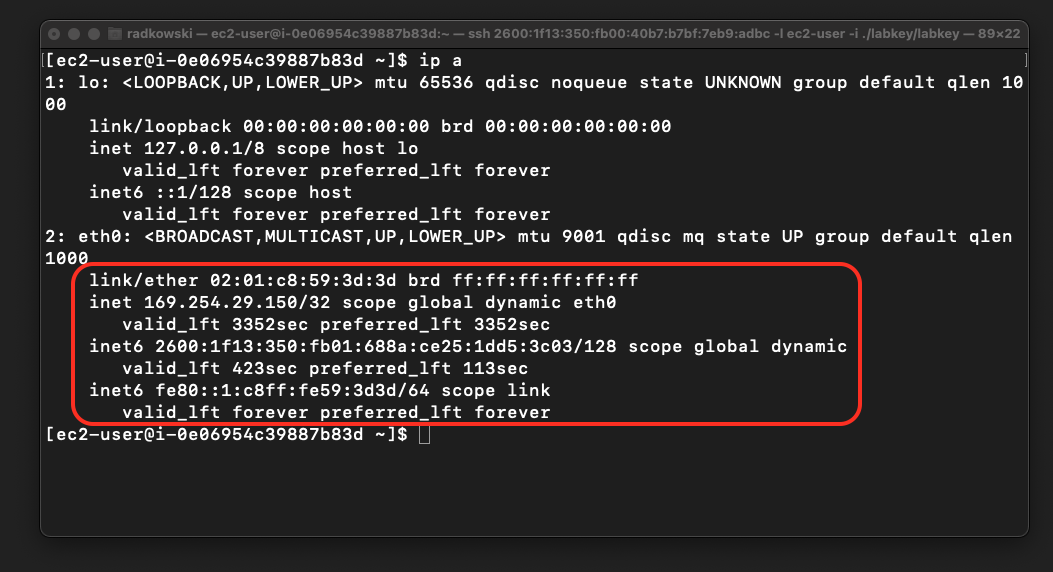
12. Check IPv6-only network configuration
Log into v6only instance. Confirm that the first network interface (eth0) doesn't have an IPv4 address configured (except 169.254.X.Y/32)
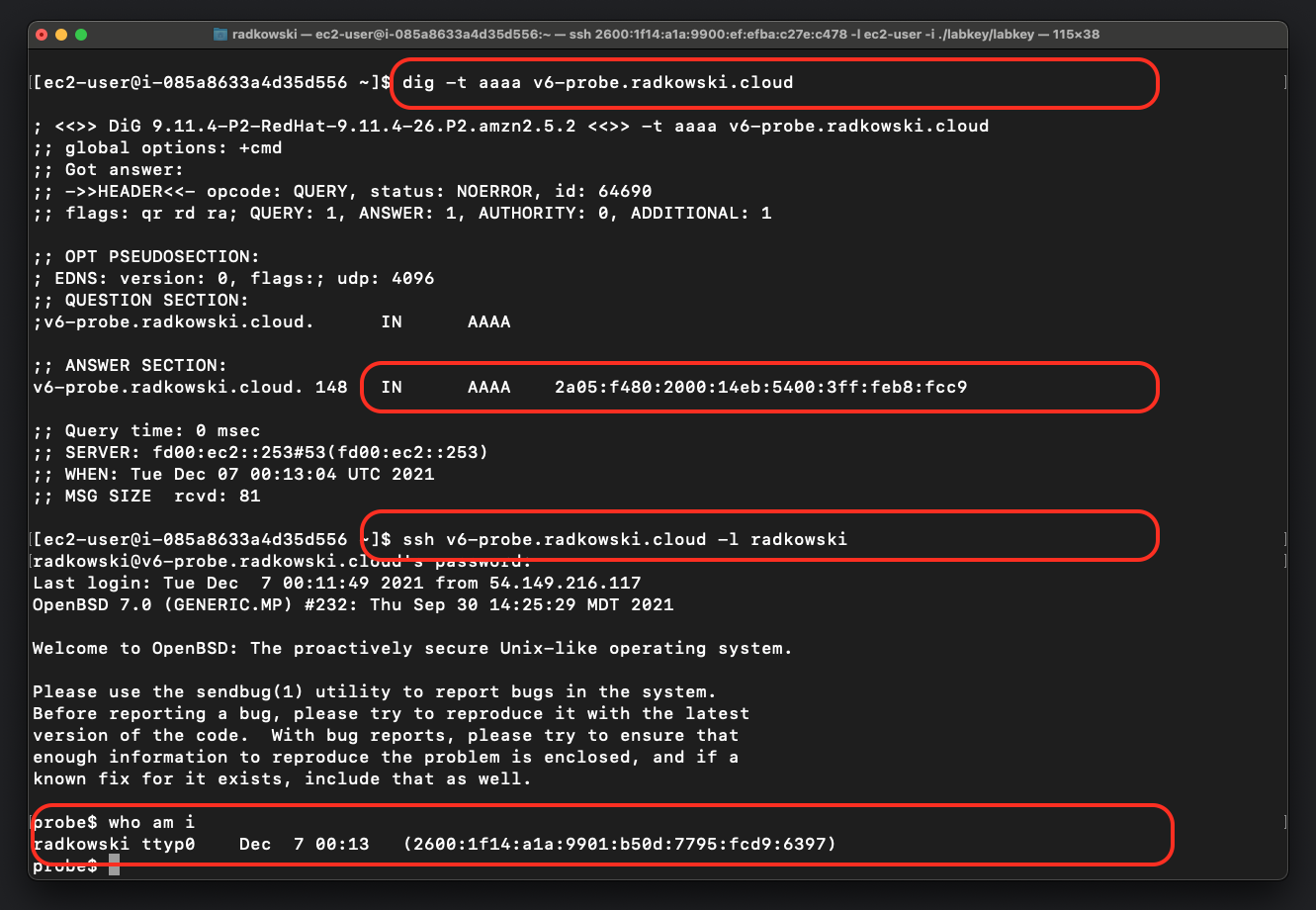
13. Connect to test instance using IPv6
Establish connection to test instance using v6-probe.radkowski.cloud. Once done, confirm that connection is established using IPv6
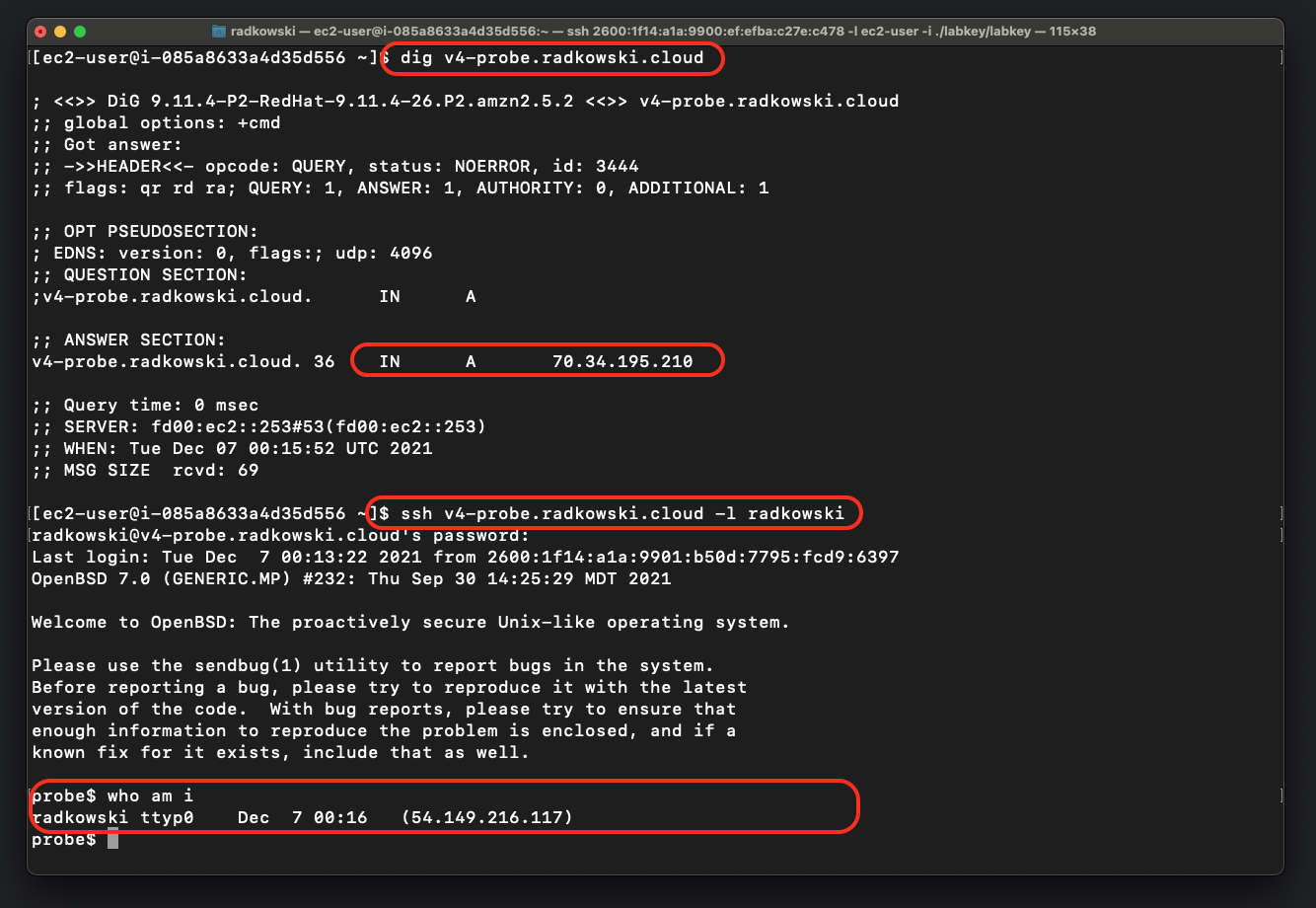
14. Confirm NAT64 works as expected
Establish connection to test instance using v4-probe.radkowski.cloud. Once done, confirm that connection is established using IPv4
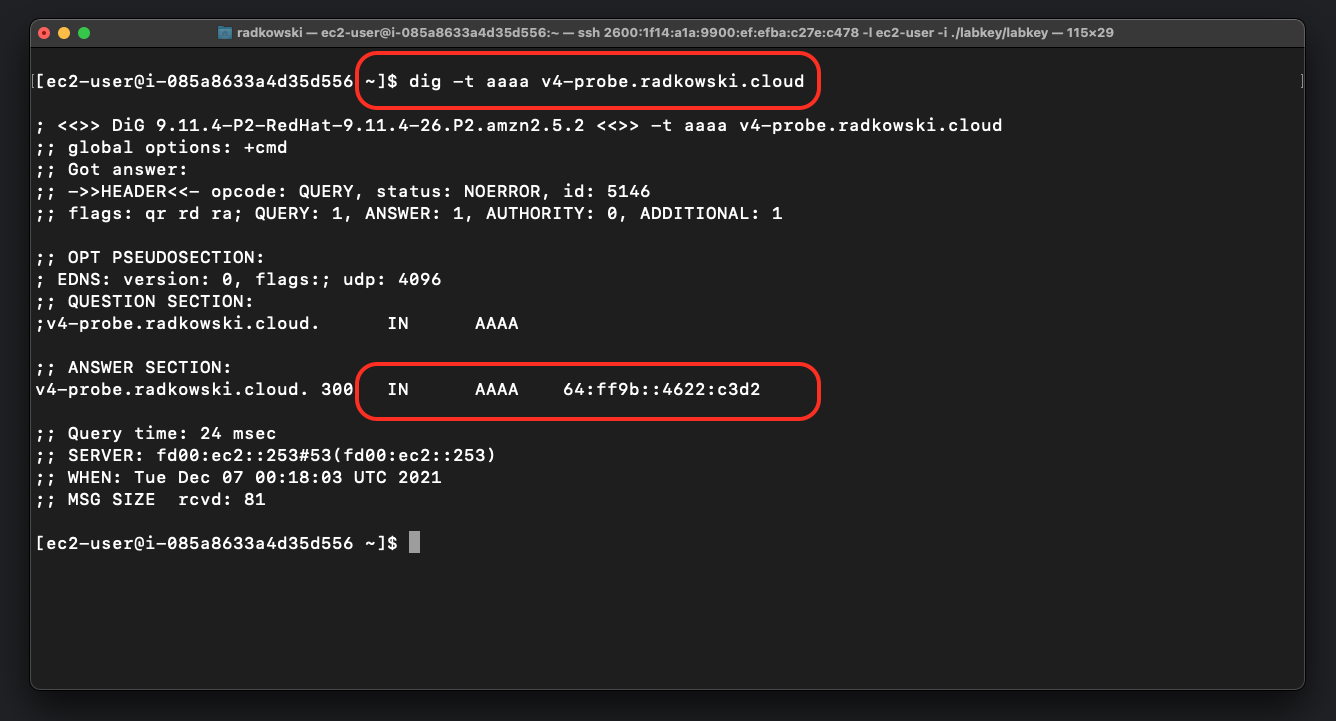
15. Confirm DNS64 works as expected
Using dig command check AAAA type response for v4-probe.radkowski.cloud. Confirm if DNS64 works as expected and IPv4 address has been translated into RFC6052 64:ff9b::/96 (RFC6052)
16. Confirm traffic is properly nated using NATGW
Check Elastic IP associated with NATGW created in step #5 - it should be the same as source IP for IPv4 connection established in step #14