ACM PCA auto revoke
Description
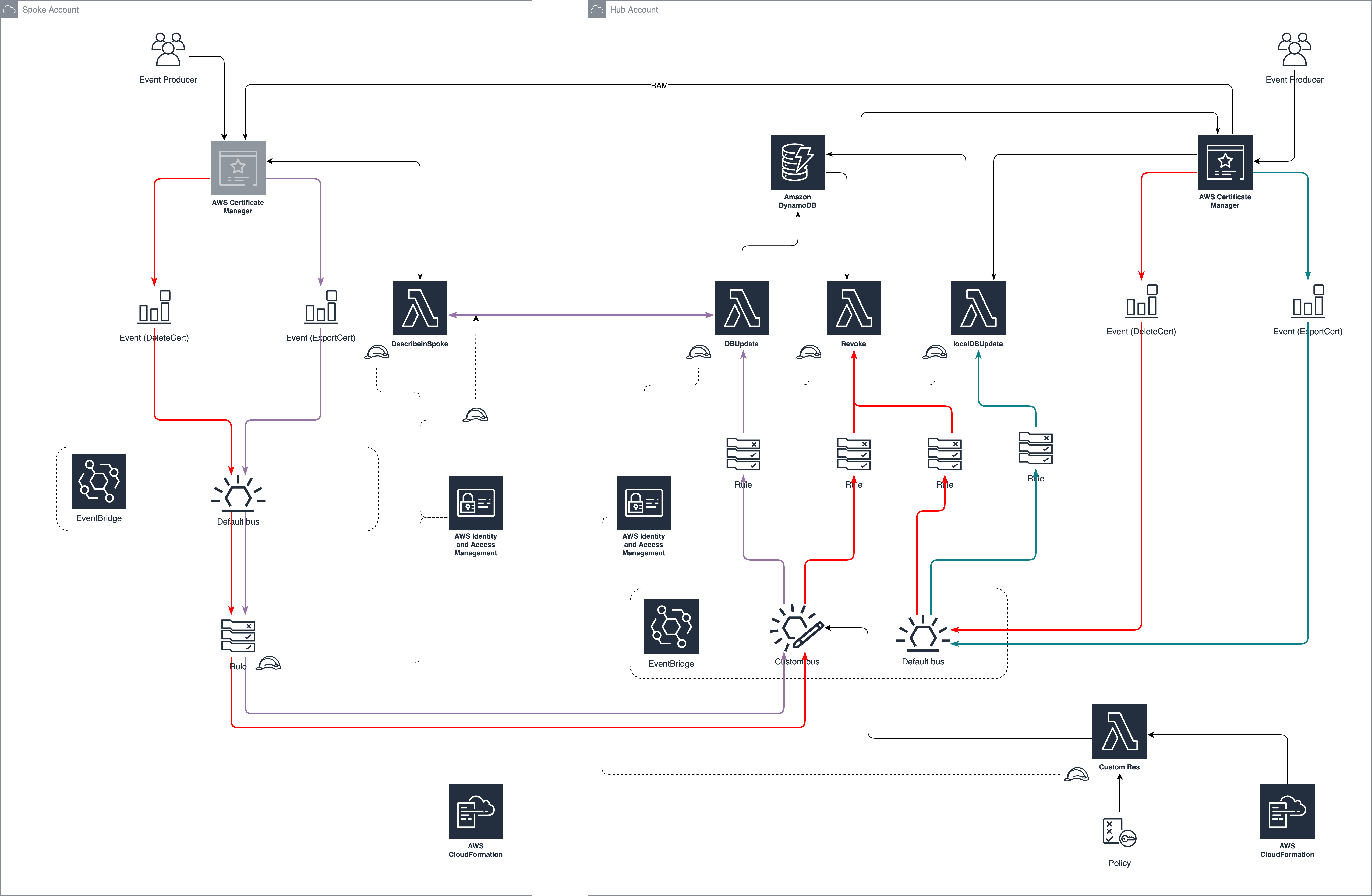
AWS Certificate Manager allows to deploy private CA. As certificates issued by privateCA can be exported, you are no longer limited to services integrated with ACM. ACM PCA can also be shared using Resource Access Manager, which makes solution to be available accross multiple/all organisation accounts.
As end users can only delete but not revoke certificates, also deleted certificates are not included in CRLs, it creates potential risk when certificate will be exported and reused before deletion. Following solution address this risk: all exported certificates are tracked and recorded in isolated DynamoDB. If certificate is deleted, solution automatically revokes it.
Solution Schema
IaC
Resources list
AWS Certificate Manager

Service deployed as PrivateCA
AWS IAM

Service used to configure roles/policies used by solution. There are 4 roles in hub account and three in each spoke account.
Hub account: one role per each lambda
Spoke account:
- one role for local lambda
- one role for EventBridge rule to allow sending events between accounts
- one role to be assumed by lambda in hub account
Amazon EventBridge
Service used to filter DeleteCert and ExportCert events. Solution implements custom bus in hub account to track all events accross all spoke accounts.
Amazon DynamoDB

Dedicated table to record following data:
- certificate ARN
- certificate serial
- Event date
- Requester info
Above information is used to track all certificates (both on hub and spoke accounts) which has been exported.
AWS Lambda

Hub account:
- localDBUpdate: update DynamoDB based on request from hub account, only
- DBUpdate: DynamoDB update, based on events from spoke accounts
- Revoke: certificate revocation lambda, based on data queried from DynamoDB
- Custom Policy: used as CF Custom Resource to set event bus policy
Spoke account(s):
- DescribeCert: lambda to describe certificate and record serial number based on ARN