CloudFormation drift detection
Description
AWS CloudFormation drift detection is a powerful feature that allows addressing the situation when resources controlled and originally deployed using stack has been modified outside the CloudFormation (for example manually using AWS Console).
Drift can be detected on an entire stack or on a particular resource(s). This information can be used to provide necessary changes to bring the resource back into compliance, as appropriate.
The above feature can be triggered as a part of AWS Config Manager Rule which checks periodically stack(s) compliance.
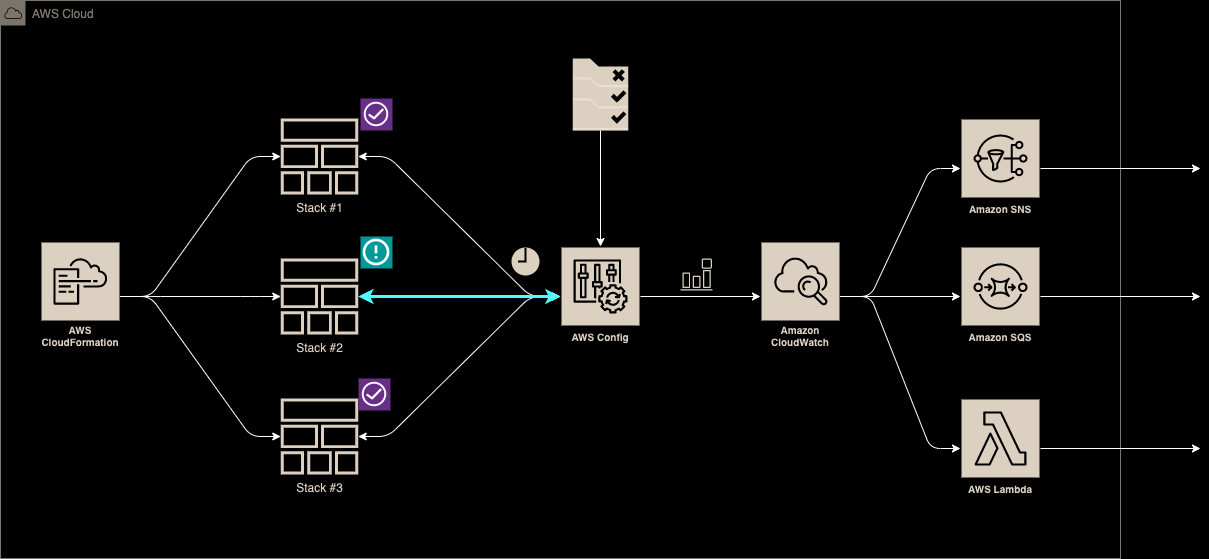
Solution Schema
IaC
Resources List
ConfigRole

IAM role including inline policy to be assumed by AWS Config.
ConfigRule

AWS Config managed rule to detect CloudFormation drift in selected stacks (tagged by KEY/VALUE defined in parameters)
CWEventTrigger
EventBridge Trigger used to trigger Lambda/SQS/SNS once CF drift is detected
Test Area
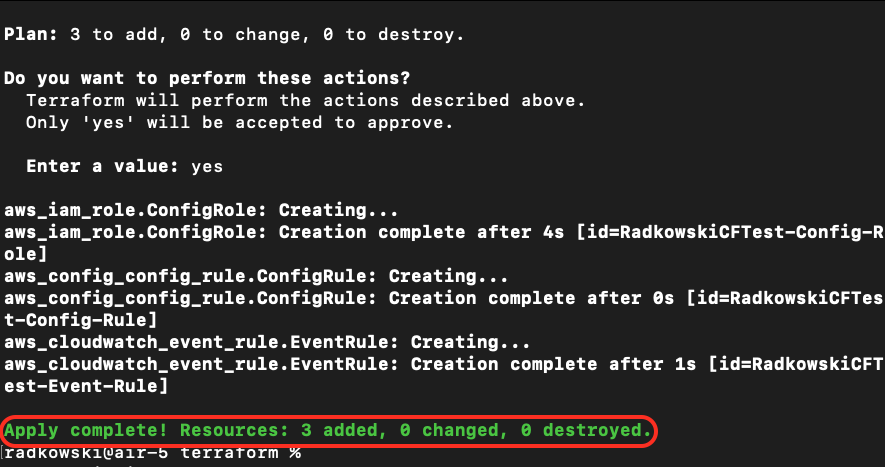
1.Deploy the solution
Use scripts located in terraform or cloudformation to deploy solution in your environment.
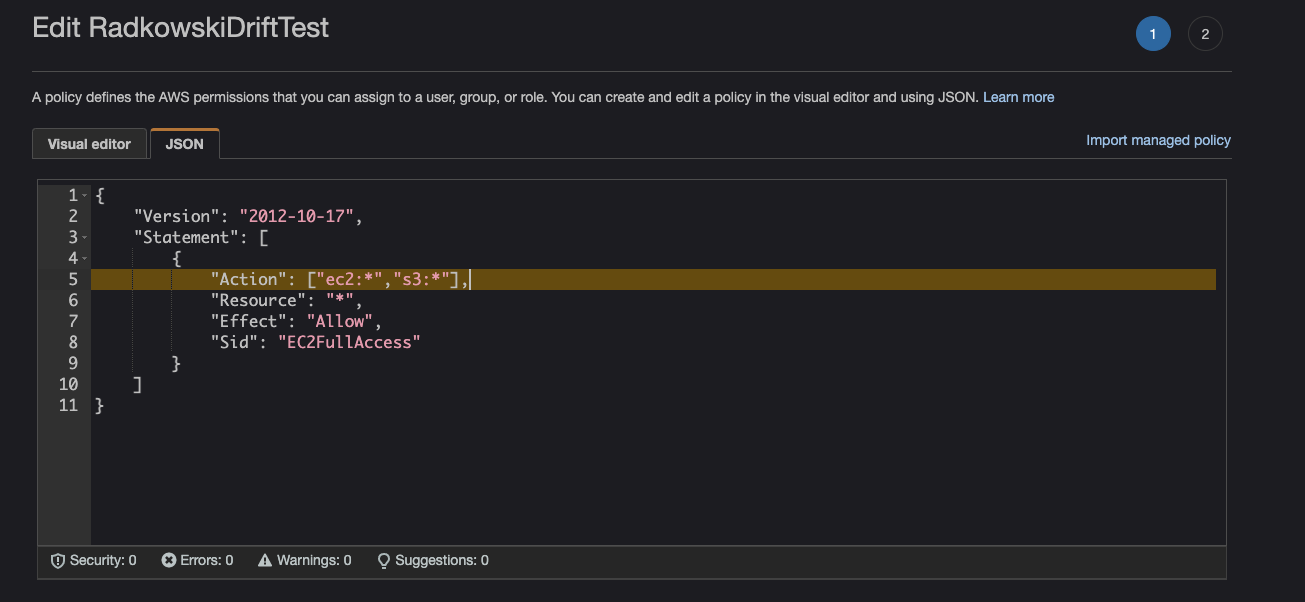
3.Deploy test CloudFormation stack
Using following code deploy example CloudFormation stack.
Resources:
RadkowskiTestPolicy:
Type: "AWS::IAM::ManagedPolicy"
Properties:
ManagedPolicyName: "RadkowskiDriftTest"
PolicyDocument:
Version: "2012-10-17"
Statement:
-
Sid: "EC2FullAccess"
Effect: "Allow"
Action: "ec2:*"
Resource: "*"
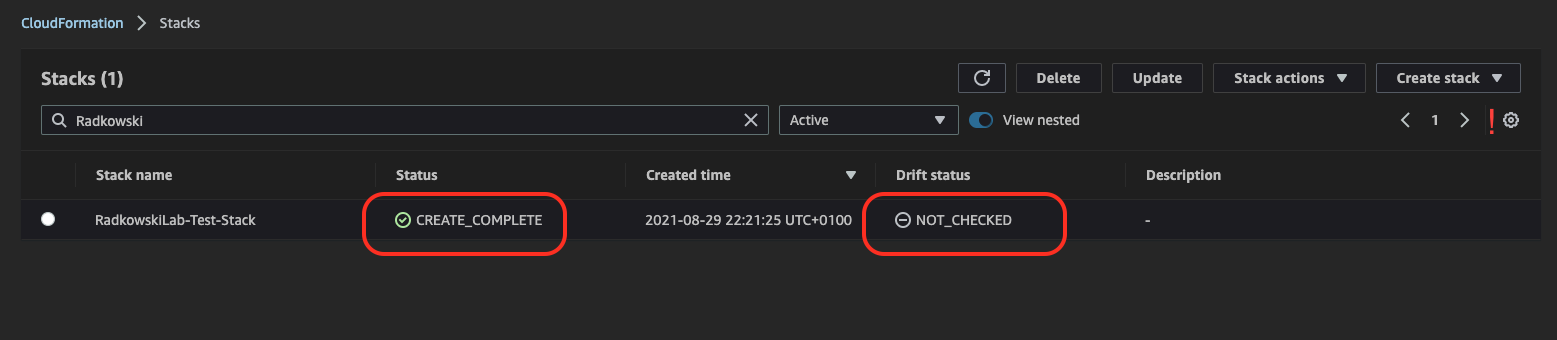
4.Check test CloudFormation stack
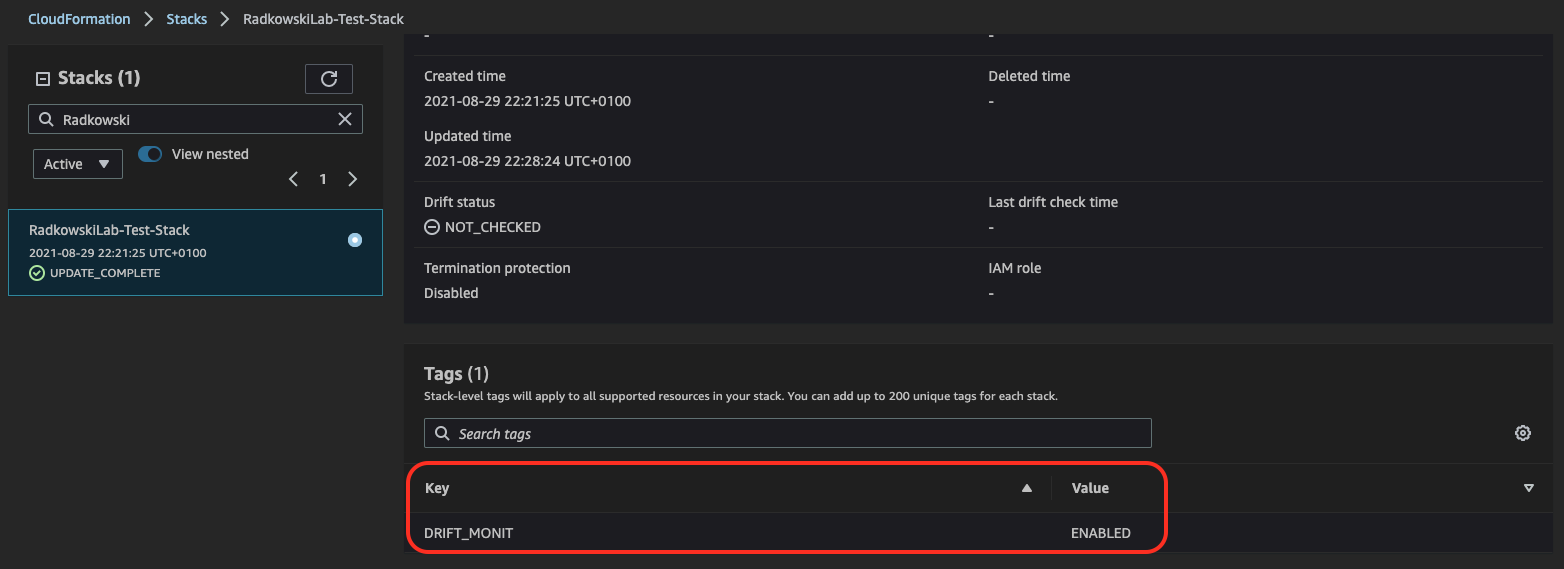
Confirm if the stack has been deployed successfully and drift status is displayed as NOT_CHECKED.
5.Check test CloudFormation stack tags
As AWS Config rule will monitor the only stack with proper tags, confirm if test stack has been configured properly.
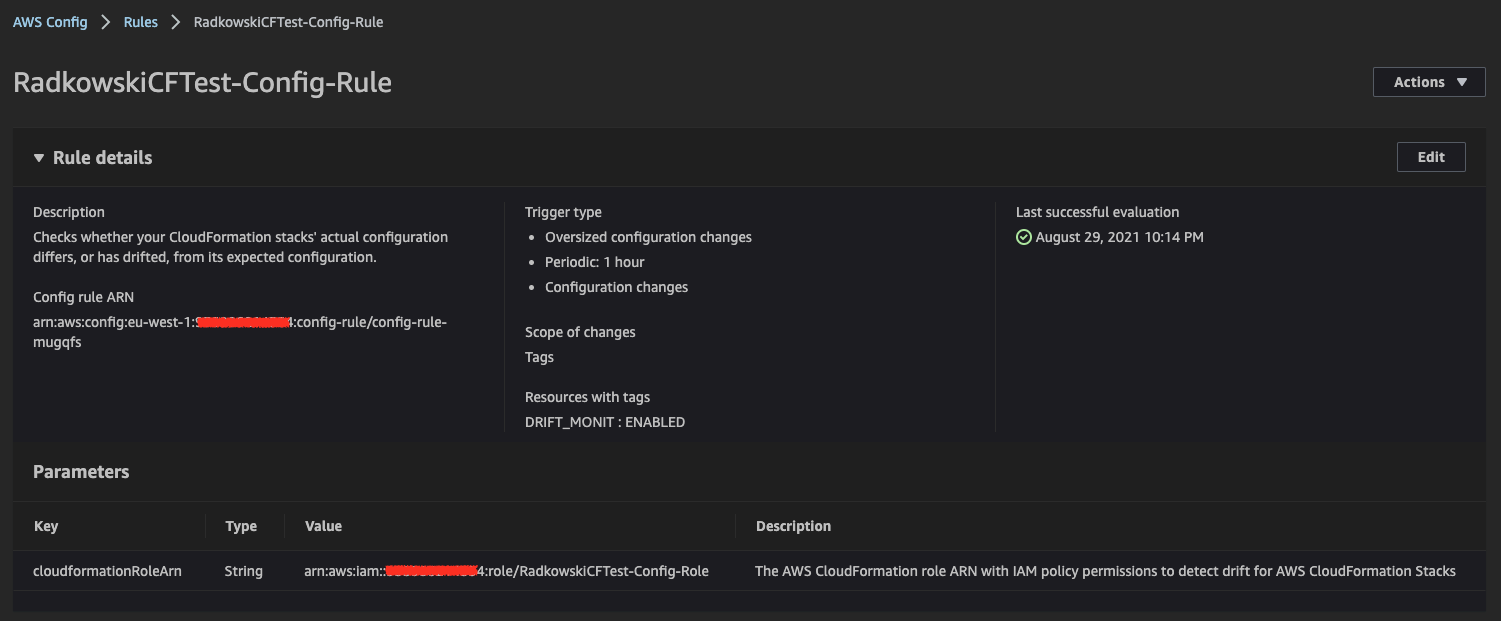
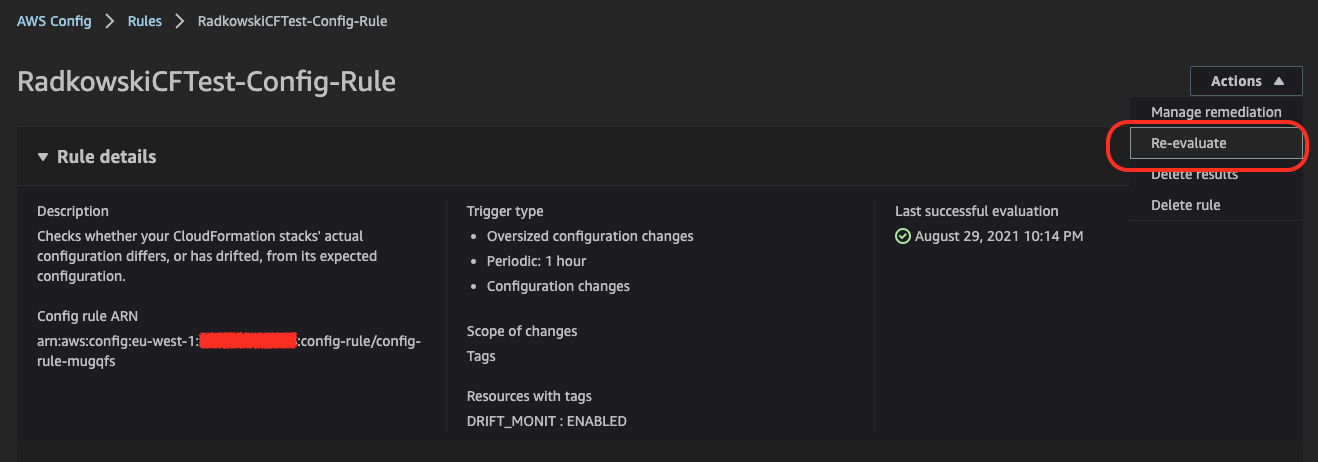
6.Re-evaluate AWS Config rule
Using AWS Config Console, re-evaluate the rule. Please bear in mind that rule will be re-evaluated every 60 mins or on-demand using AWS Console.
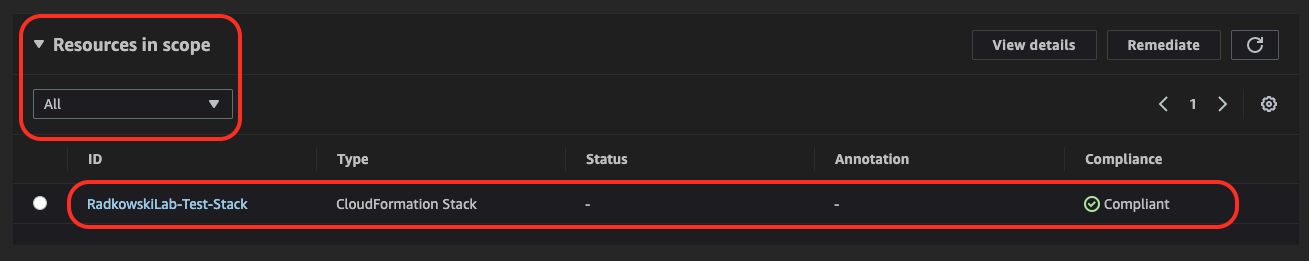
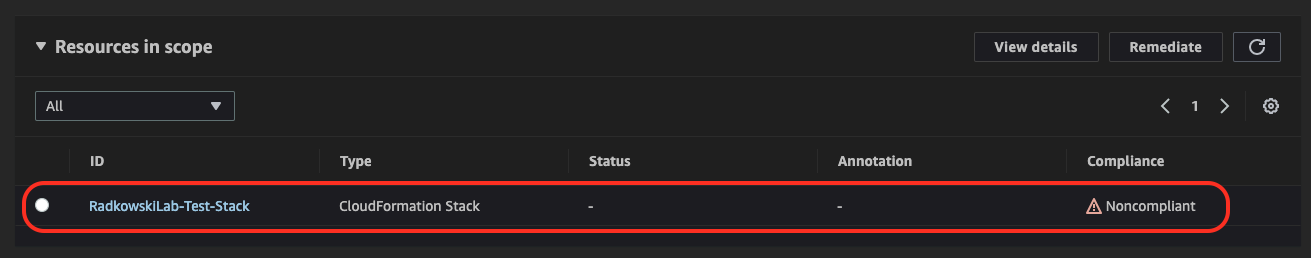
7.Check Compliance
As there were no manual changes in resources created by stack, iAWS Config should classify it as Compliant.
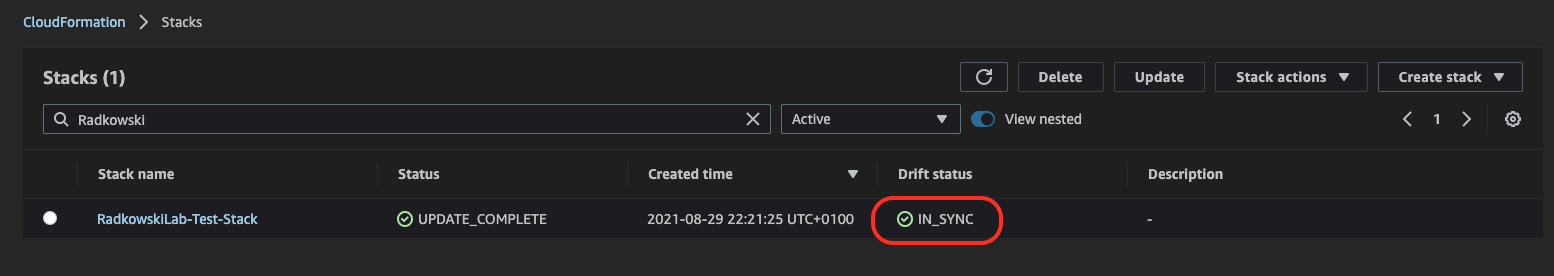
8.Check Drift Status
Come back to CloudFormation Console. Confirm, if drift status for previously created stack is IN_SYNC.
10.Re-evaluate AWS Config rule, again
Re-evaluate AWS Config rule, again. This time, resource should be marked as Noncompliant.
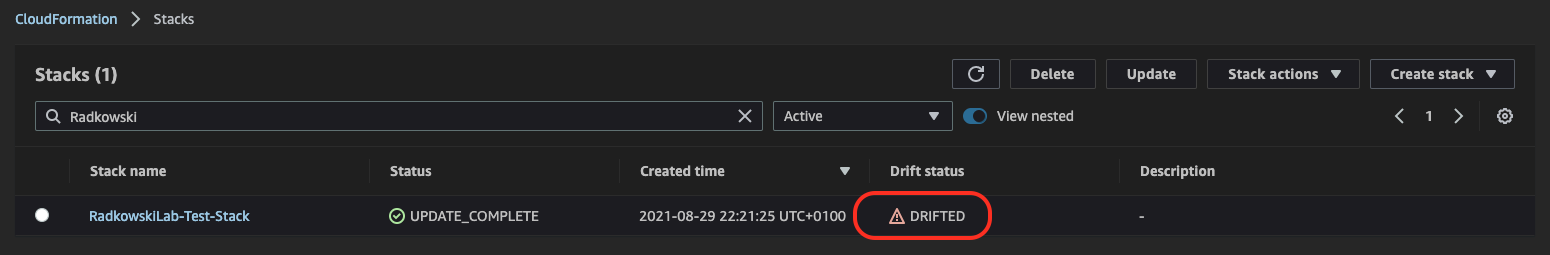
11.Check stack drift status, again
Using CloudFormation Console, check stack drift status. It should changed to DRIFTED.
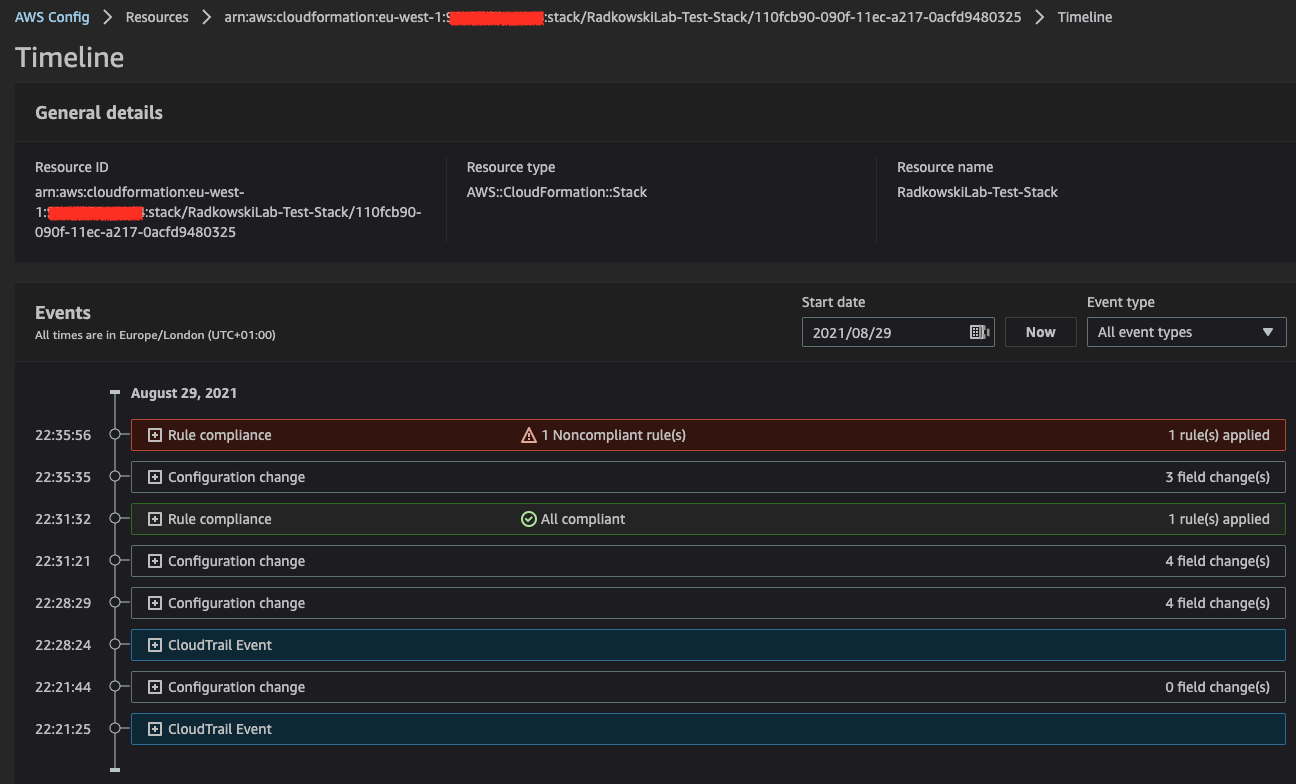
12.Display change details using Timeline
To get more details about changes, use Timeline feature from AWS Config Console.
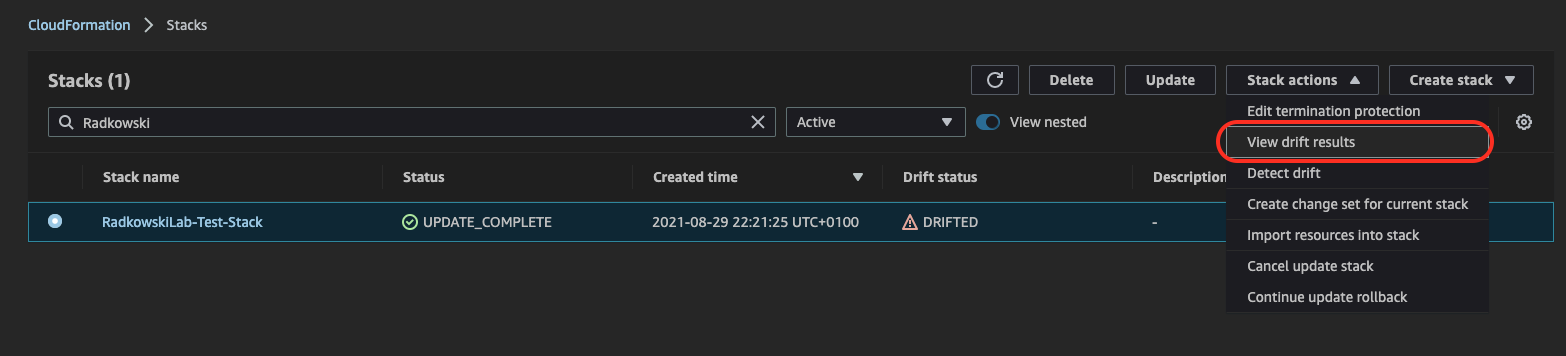
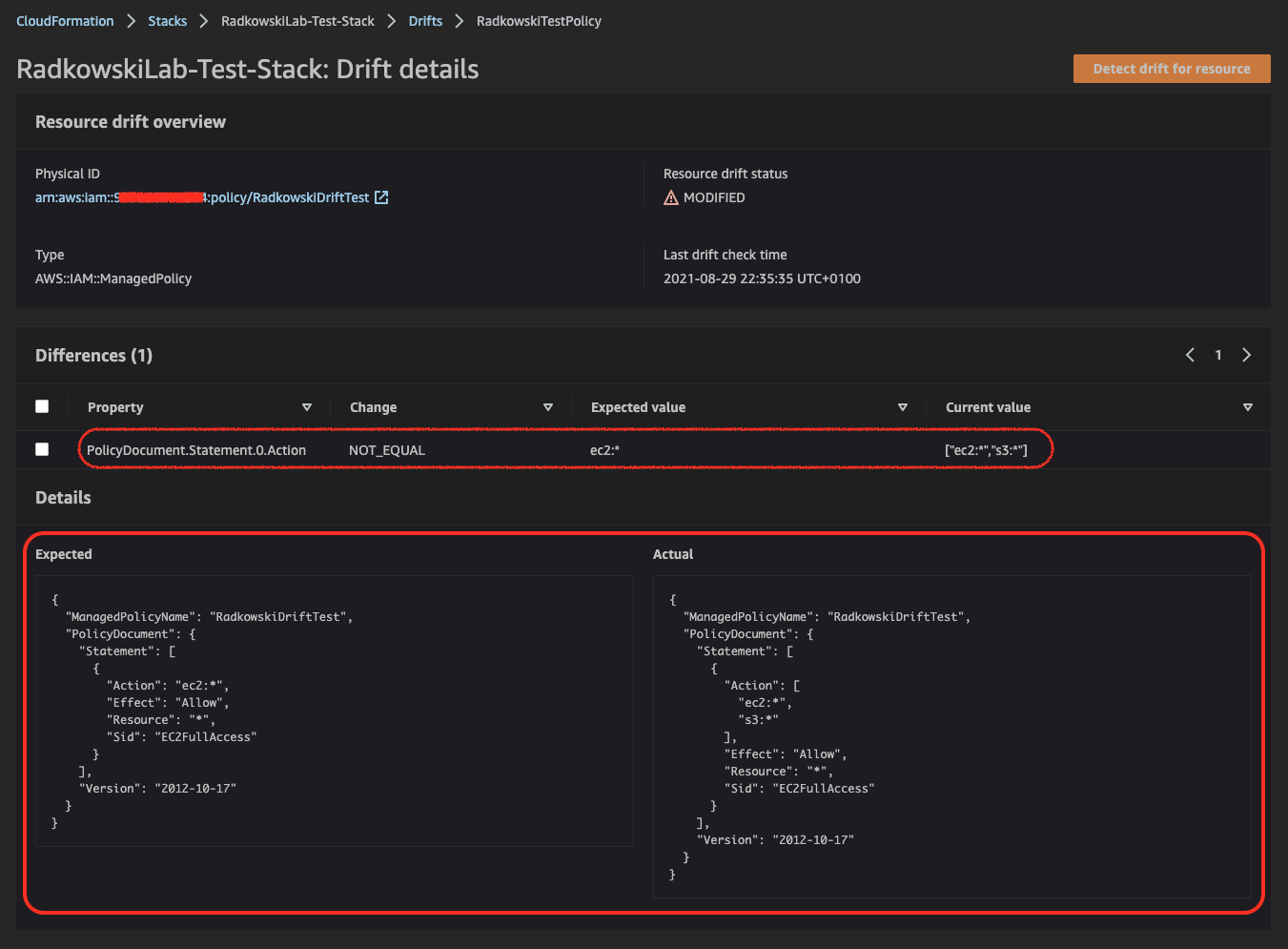
13.Display change details using drift status #1
CloudFormation Console can provide extra detailed information about drift. It can be selected using view drift results.
14.Display change details using drift status #2
Differences can be tracked directly using Expected vs Actual views.